Vulnerability Management Home Lab
Introduction
In this post, I'm going to do a Vulnerability Management Lab Where I set up a Winodws 10 inside a VM, install an old depricated Firefox and I'm gonna do a Vulnerability scan against the Virtual machine. So the ingredients that we will need:
What is a Vulnerability management
First What is a Vulnerability management ? Vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them. This, implemented alongside with other security tactics, is vital for organizations to prioritize possible threats and minimizing their attack surface.
Ensure The connectivity with the VM
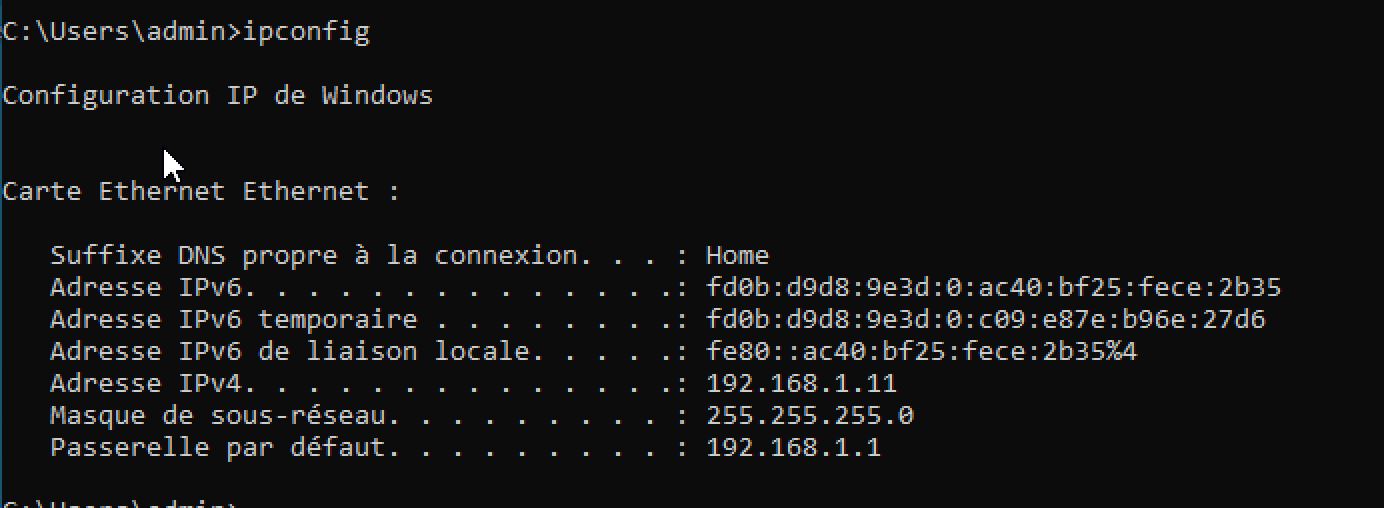
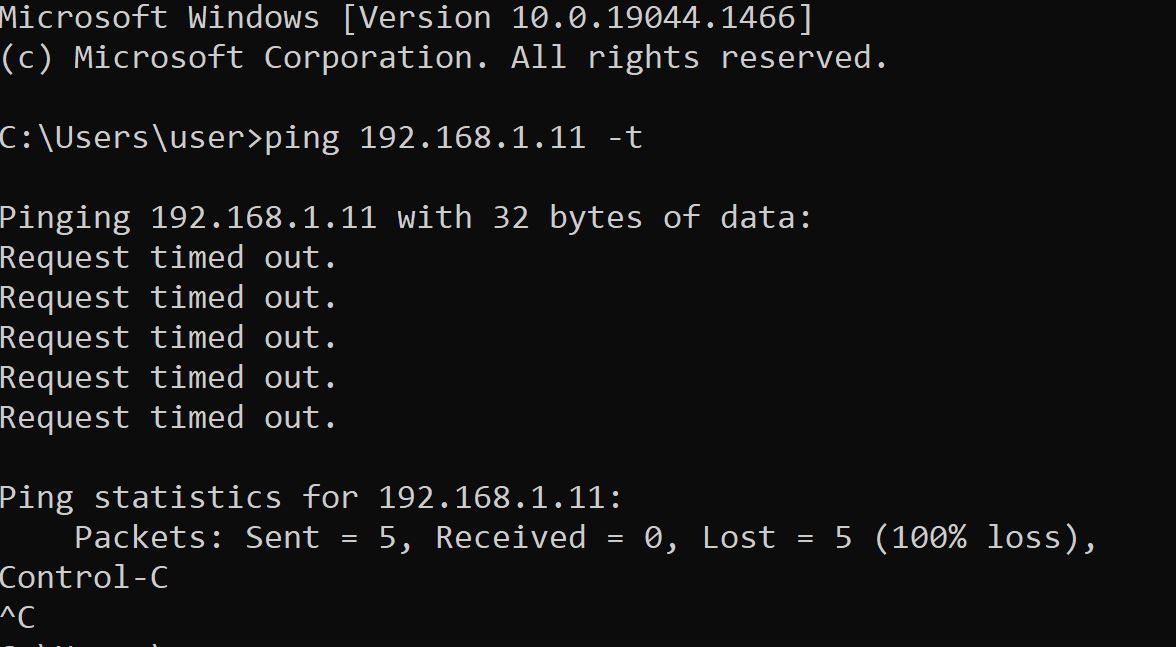
After Installing Nessus Essentials and setting up Winodws 10 inside the VM. I decided to test The connectivity with the VM;
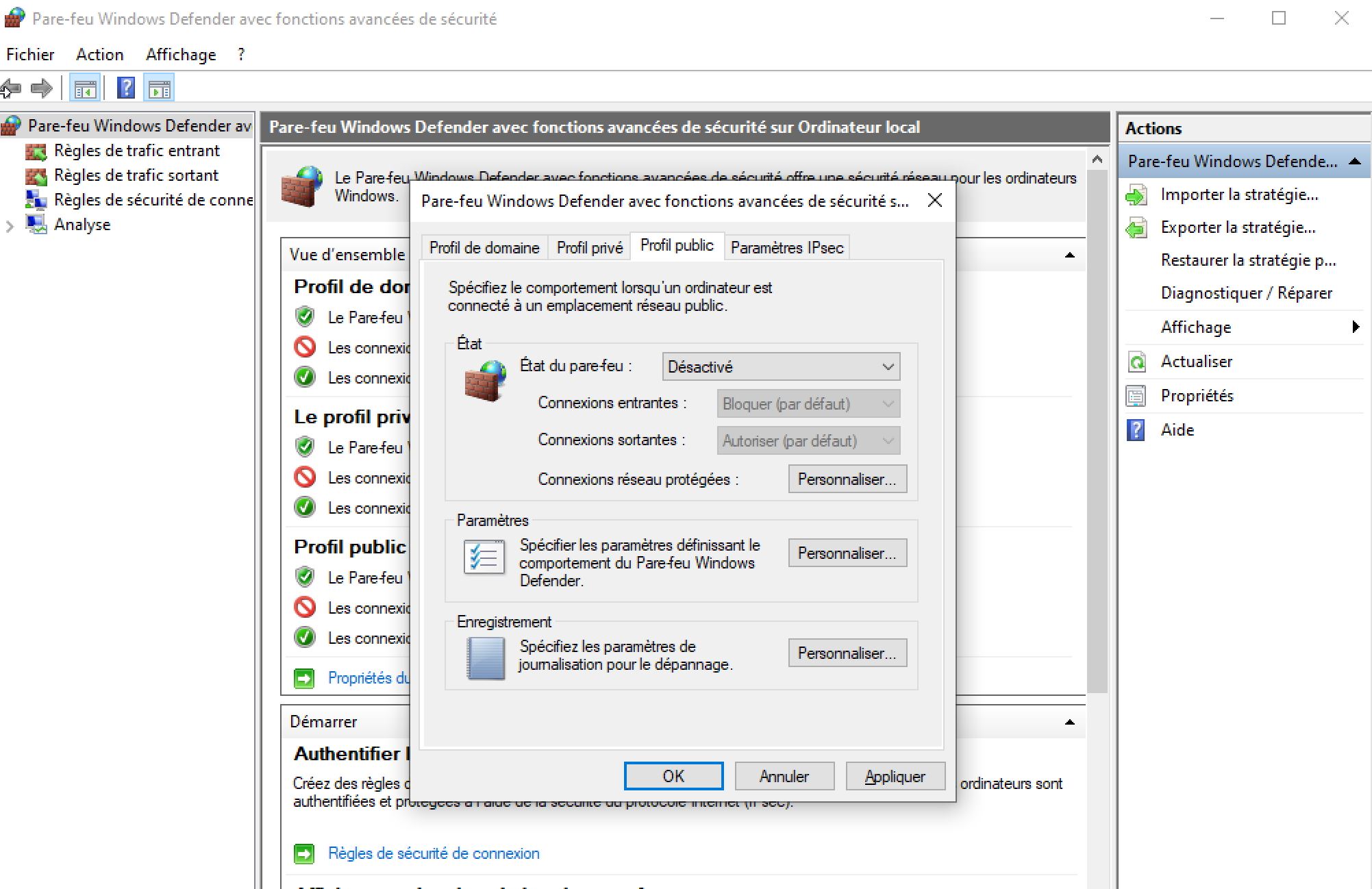
As We See the request timed out. So we have to diseable the firewall in the VM by using Microsoft Common Console Document or wf.msc.
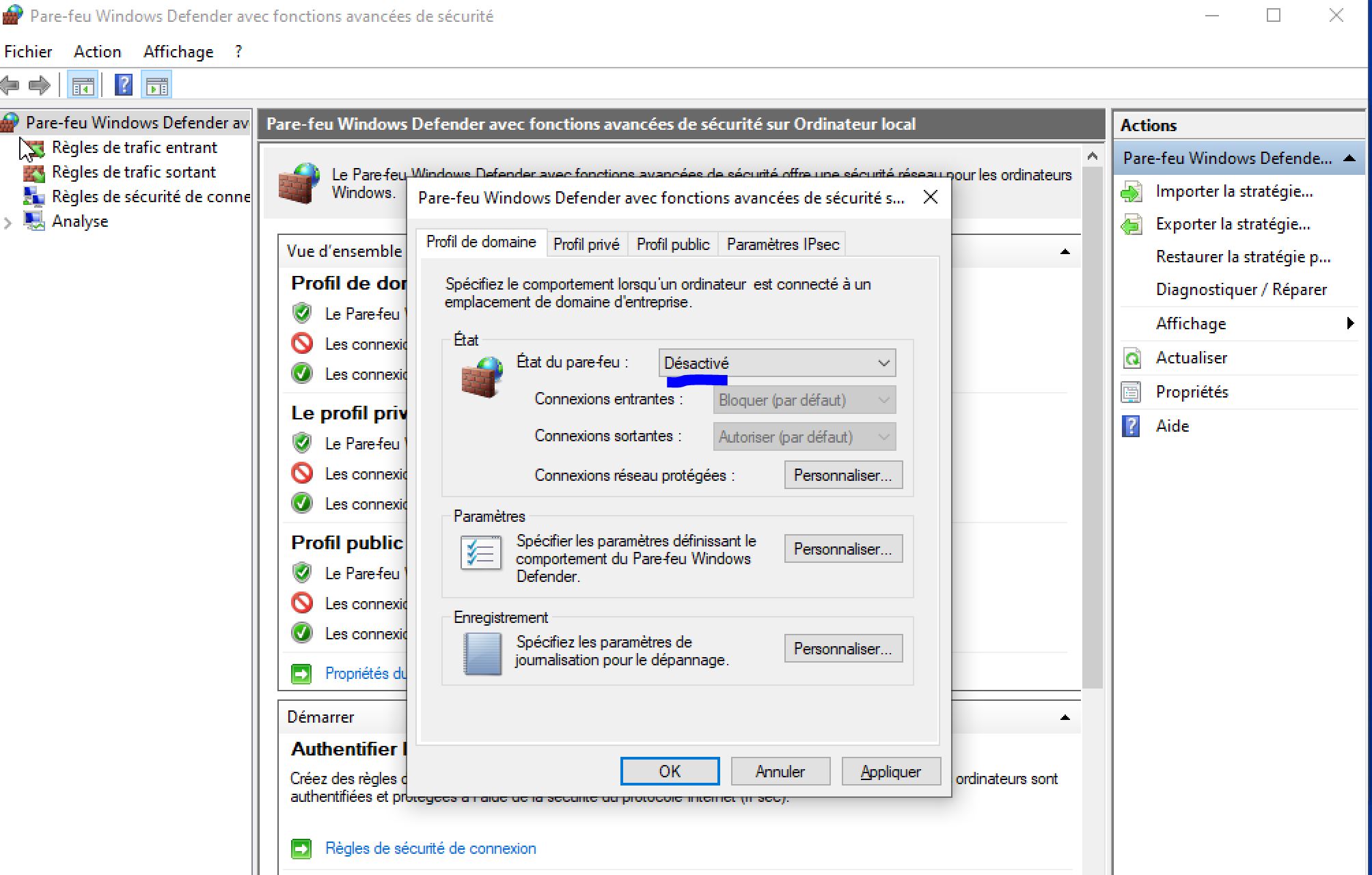
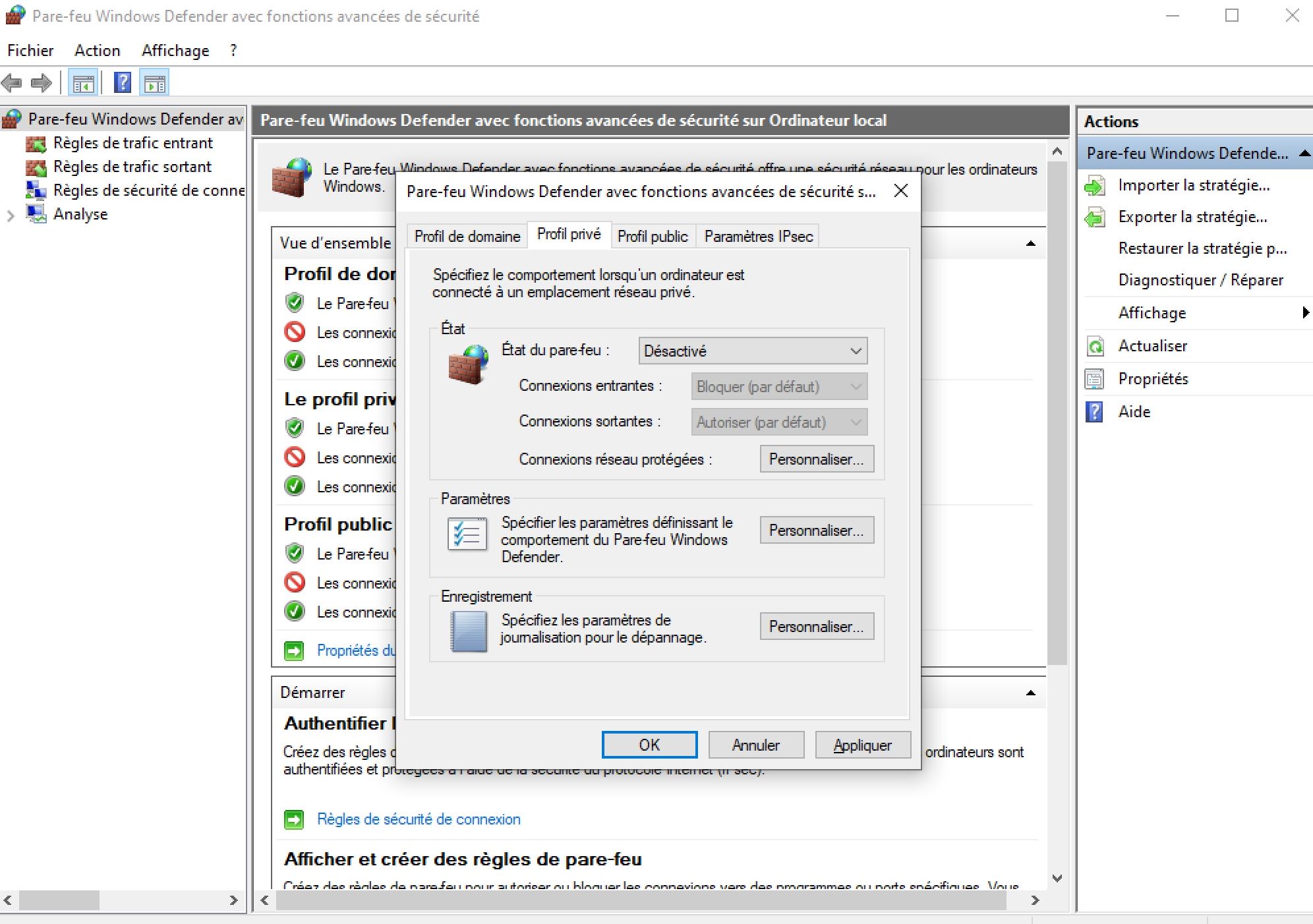
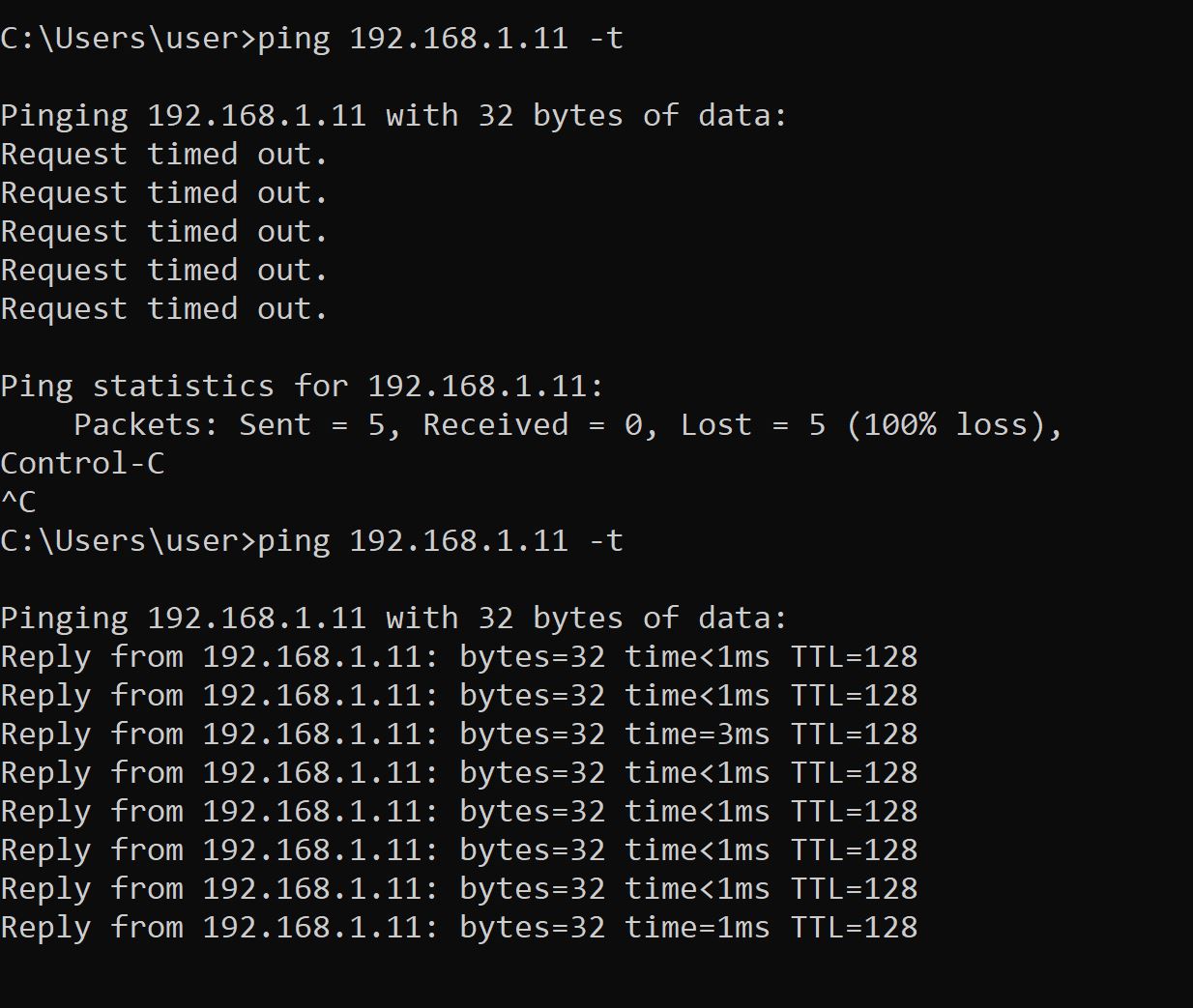
And now We can notice that the ping is going through the VM.
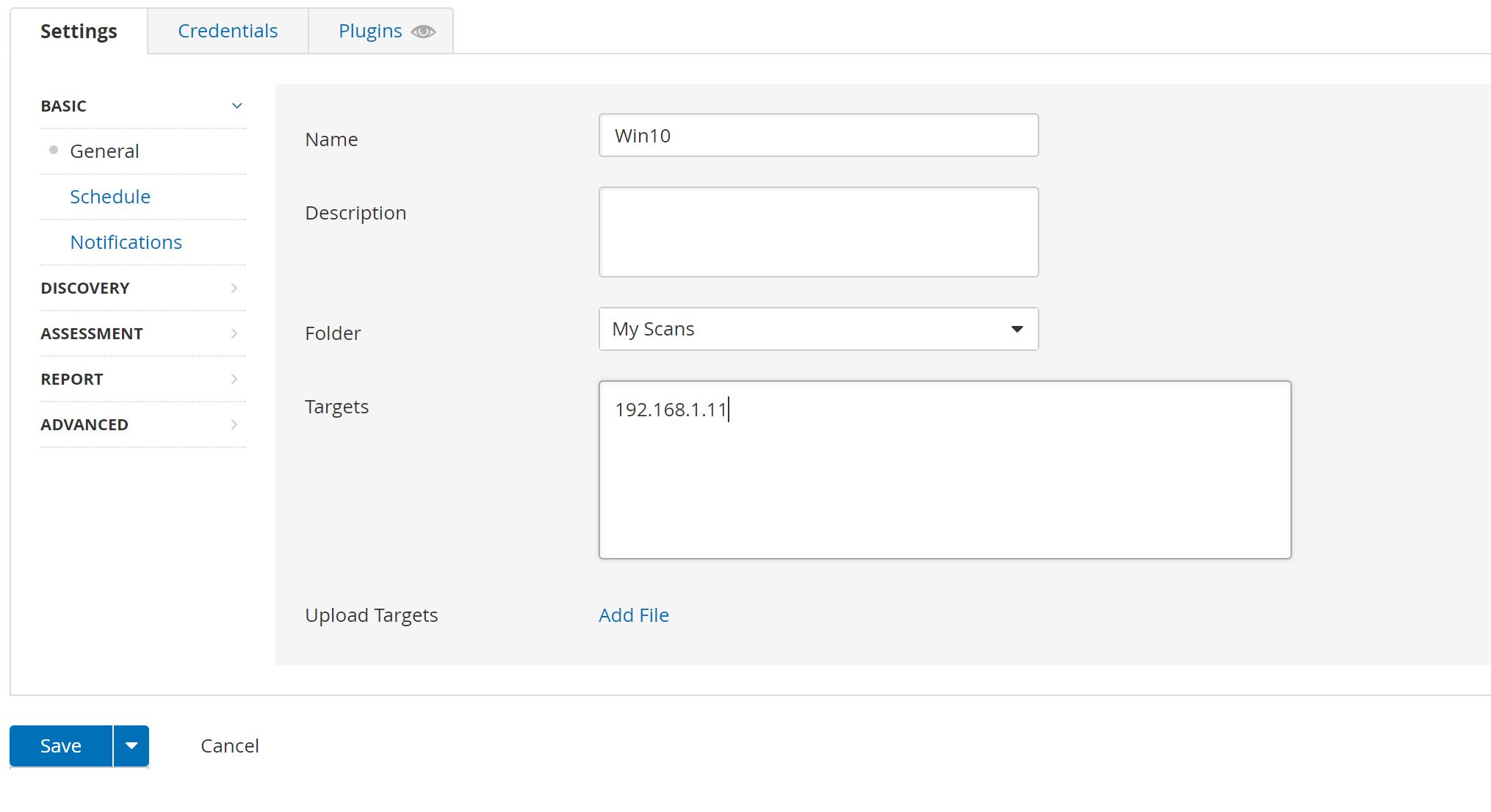
Basic Network Scan without Credentials
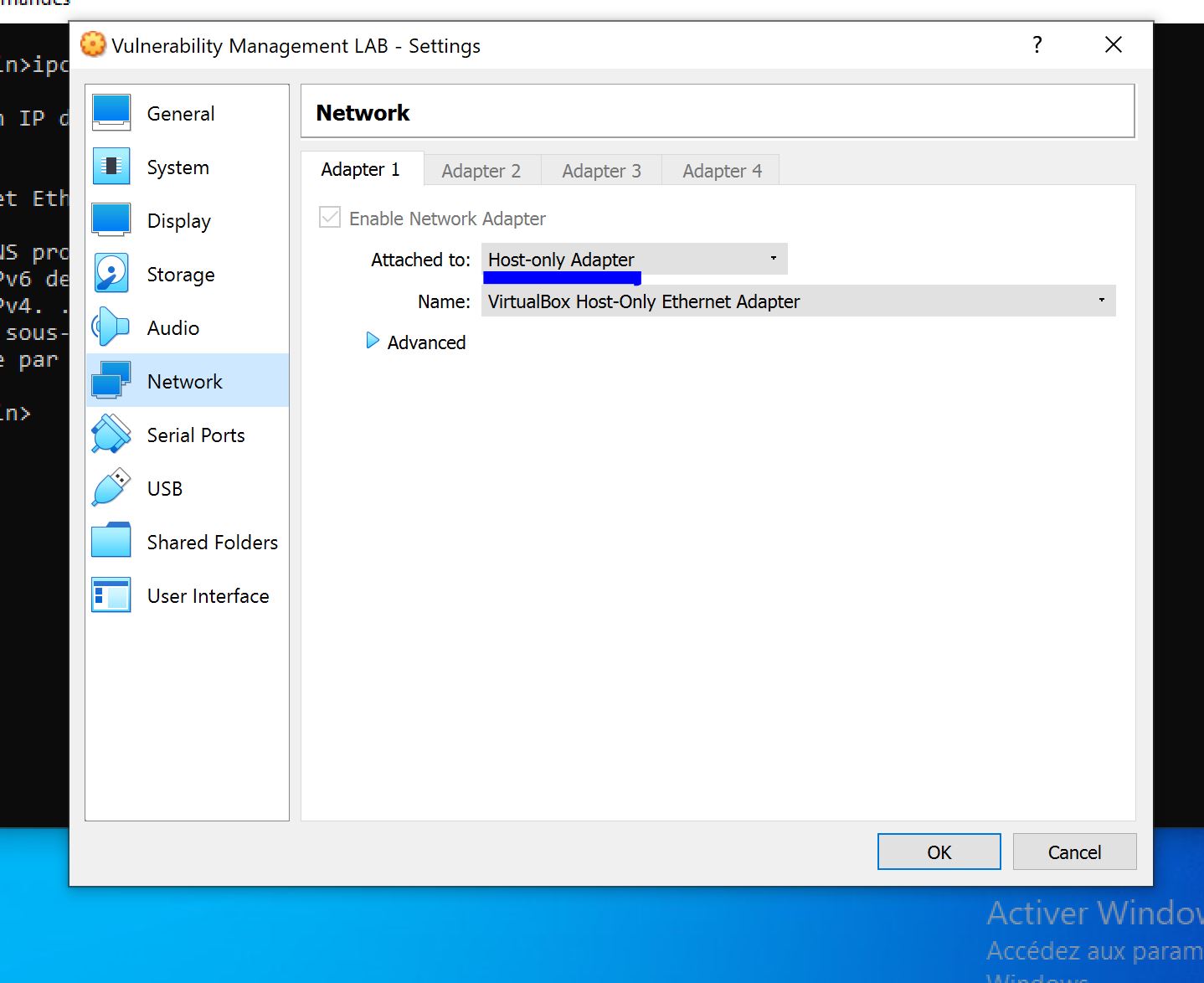
First I tried a Basic Network Scan on the Virtual machine that is connected with a network bridge But it didn't work.
And After some troubleshooting and research. I learned that Nesus have some trouble discovering bridged connected VMs and I've decided to switch to Host Only that's used to create a network containing a host without the need for the host's physical network interface. Instead, a virtual network interface.
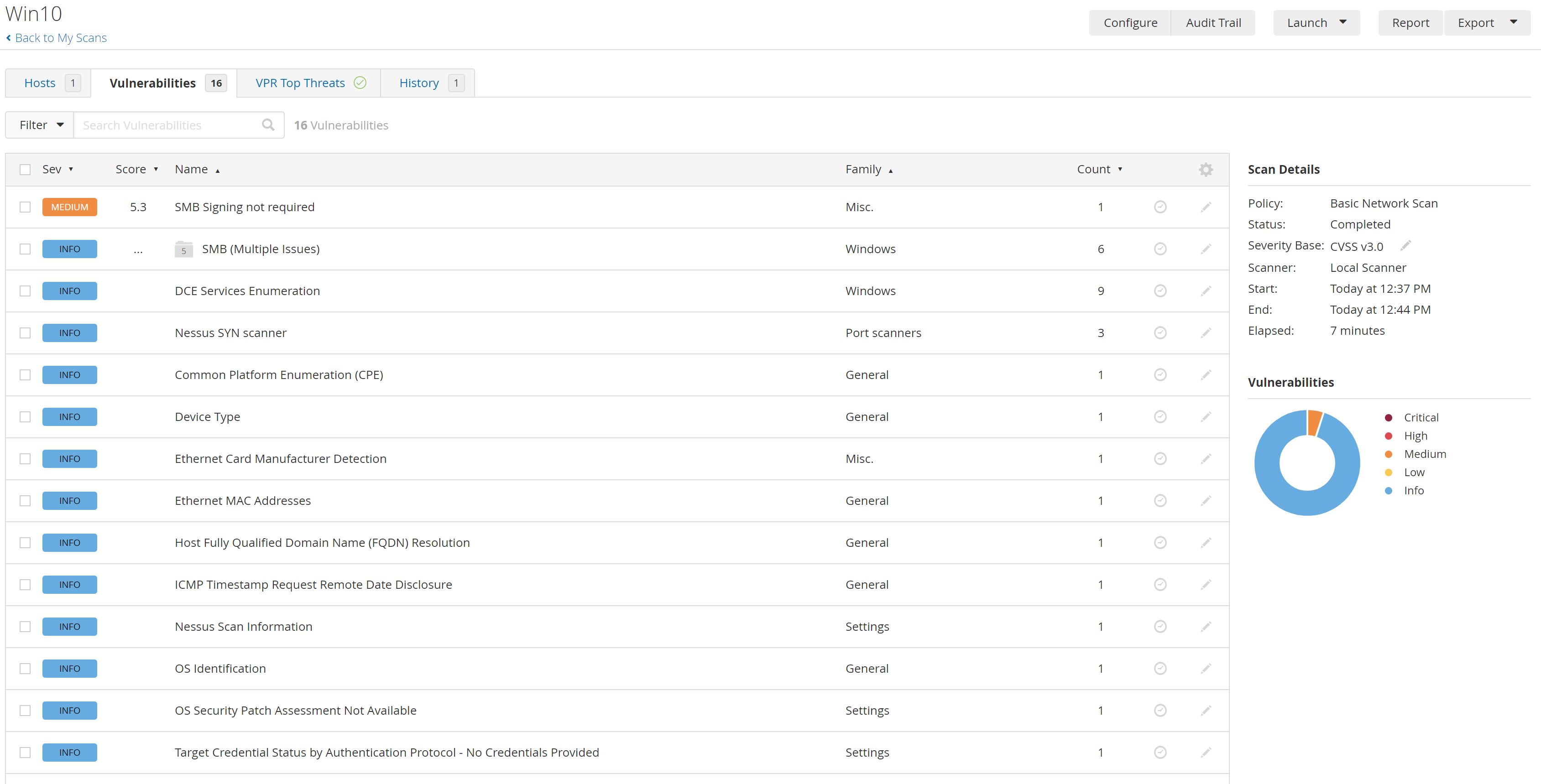
After A few minutes The scan has finished:
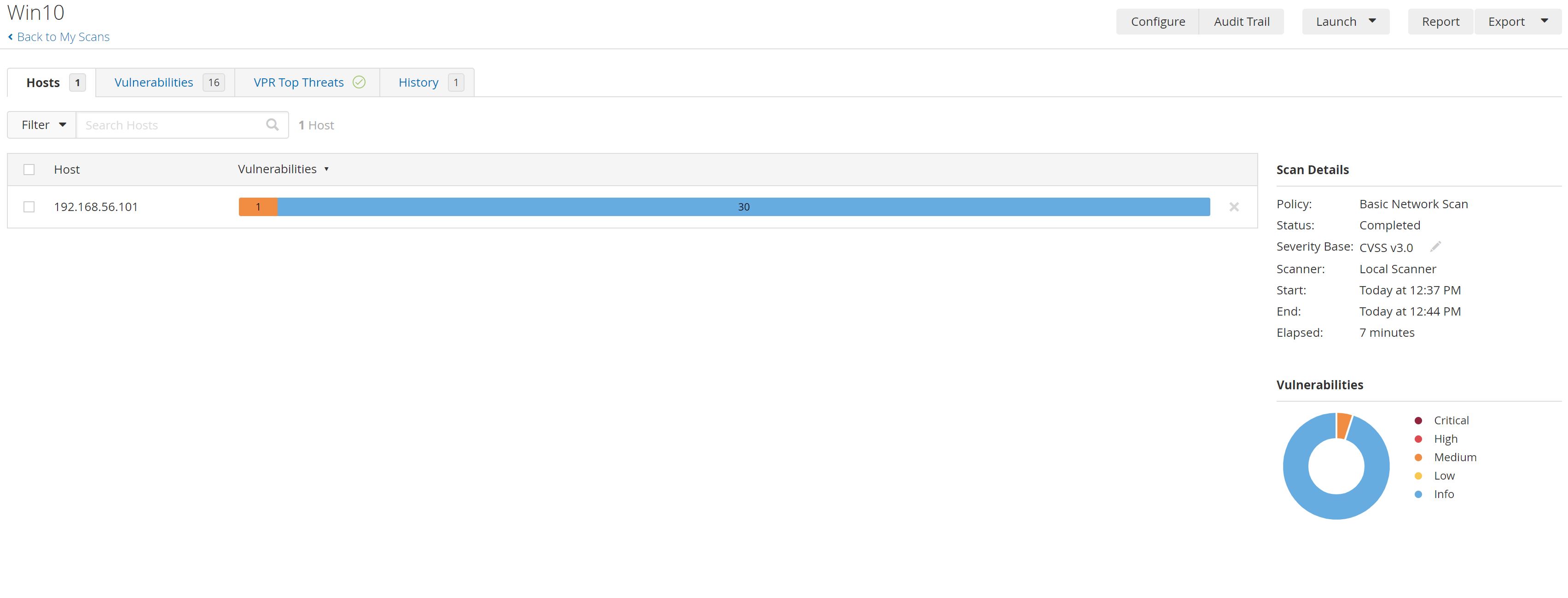
So We found 1 Medium vulnerability and 30 INFO vulnerabilities:
- SMB Signing not required: Means that an unauthenticated, remote attacker can exploit this to conduct man-in-the-middle attacks against the SMB server. See Solution
- INFO is not intended to be a vulnerability. It is simply stating a fact like a Detection an Identification etc...
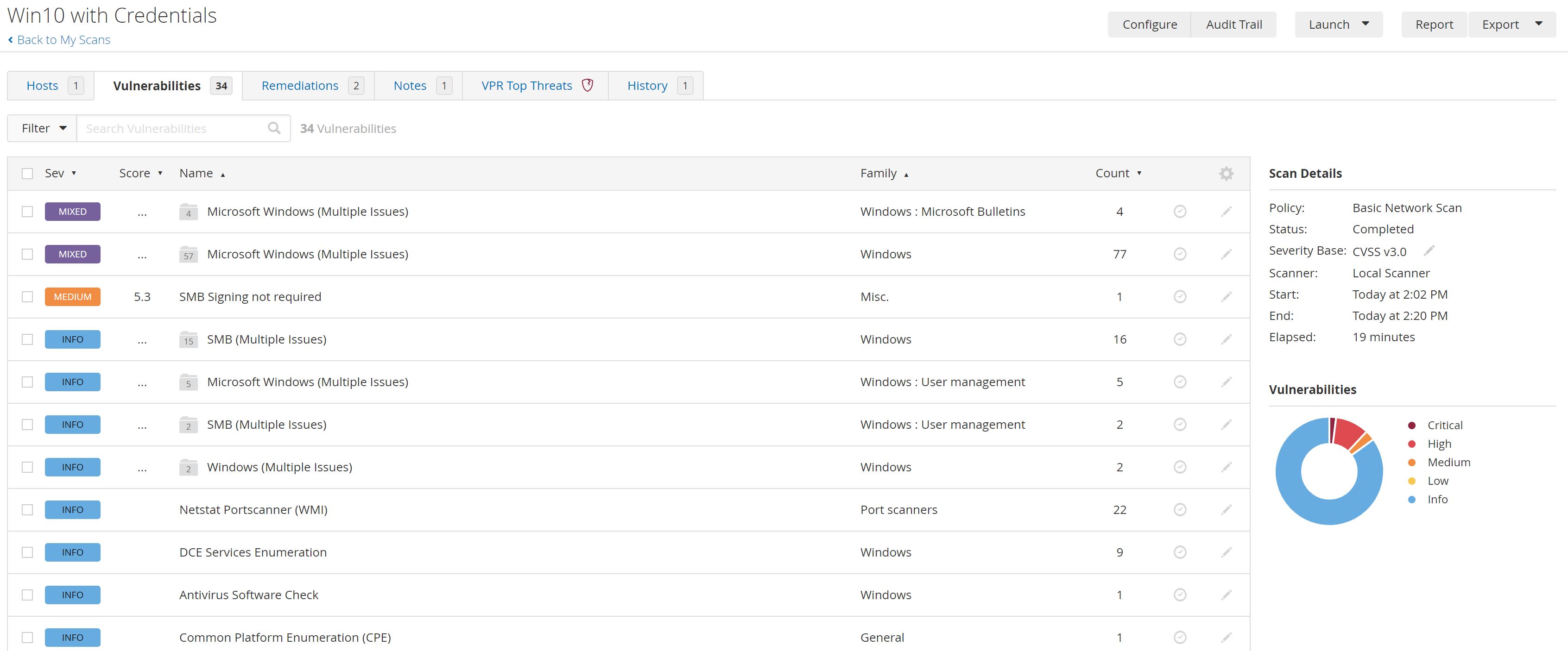
Basic Network Scan with Credentials
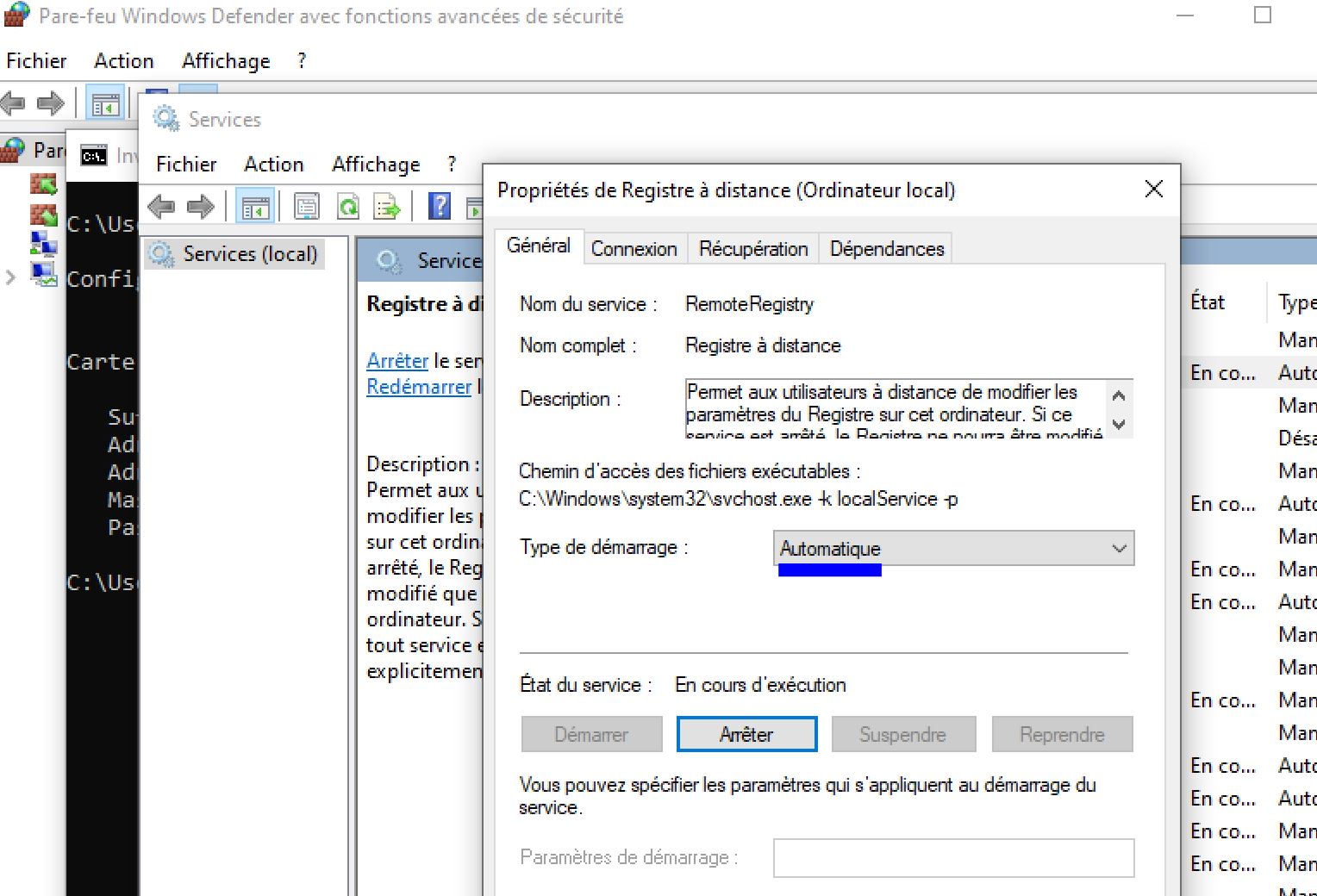
To do a credential scan we have to enable the Remote Registry which will allow the scanner to connect to the VM and look for insecure configurations.
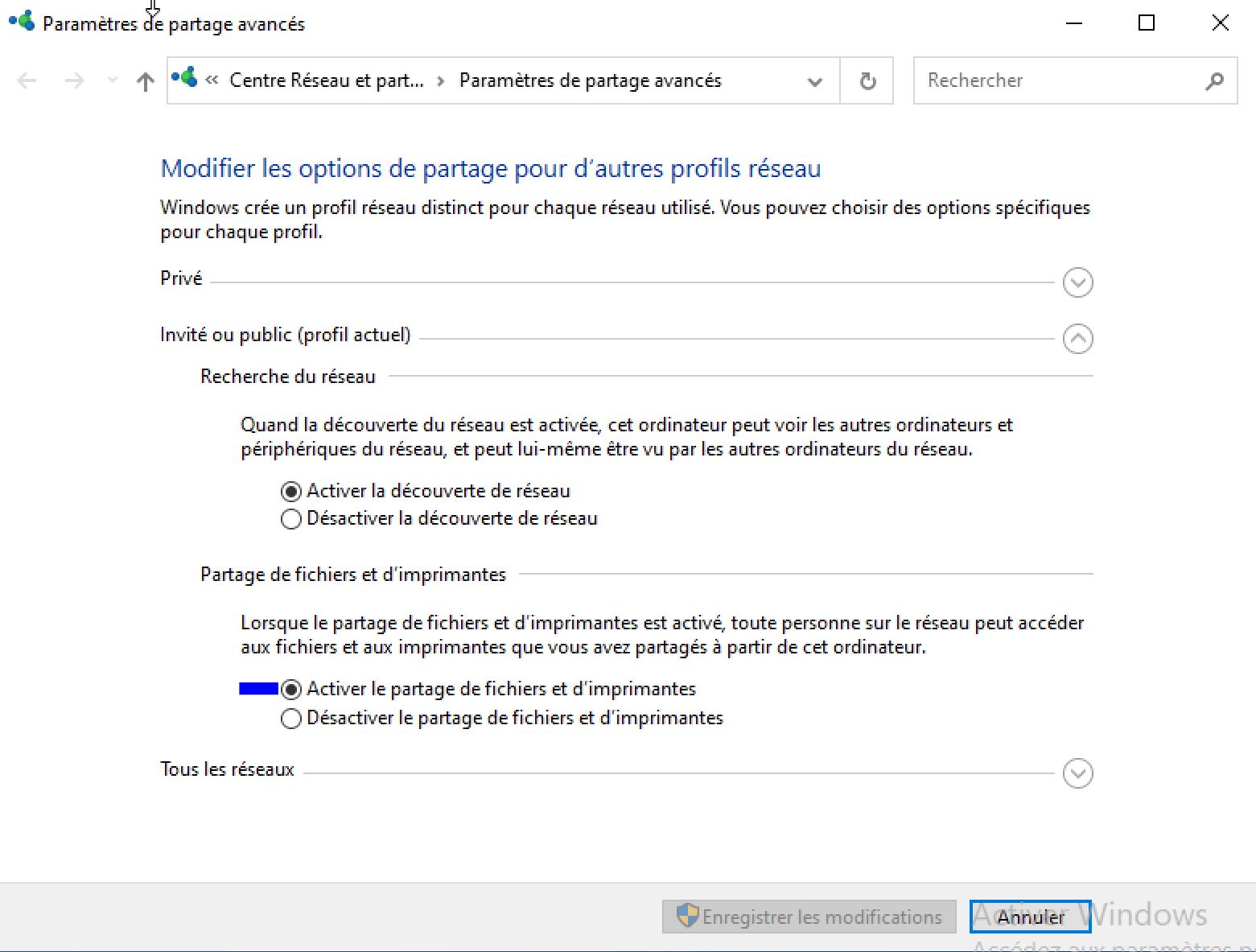
And Next we're going to enable file and printer sharing:
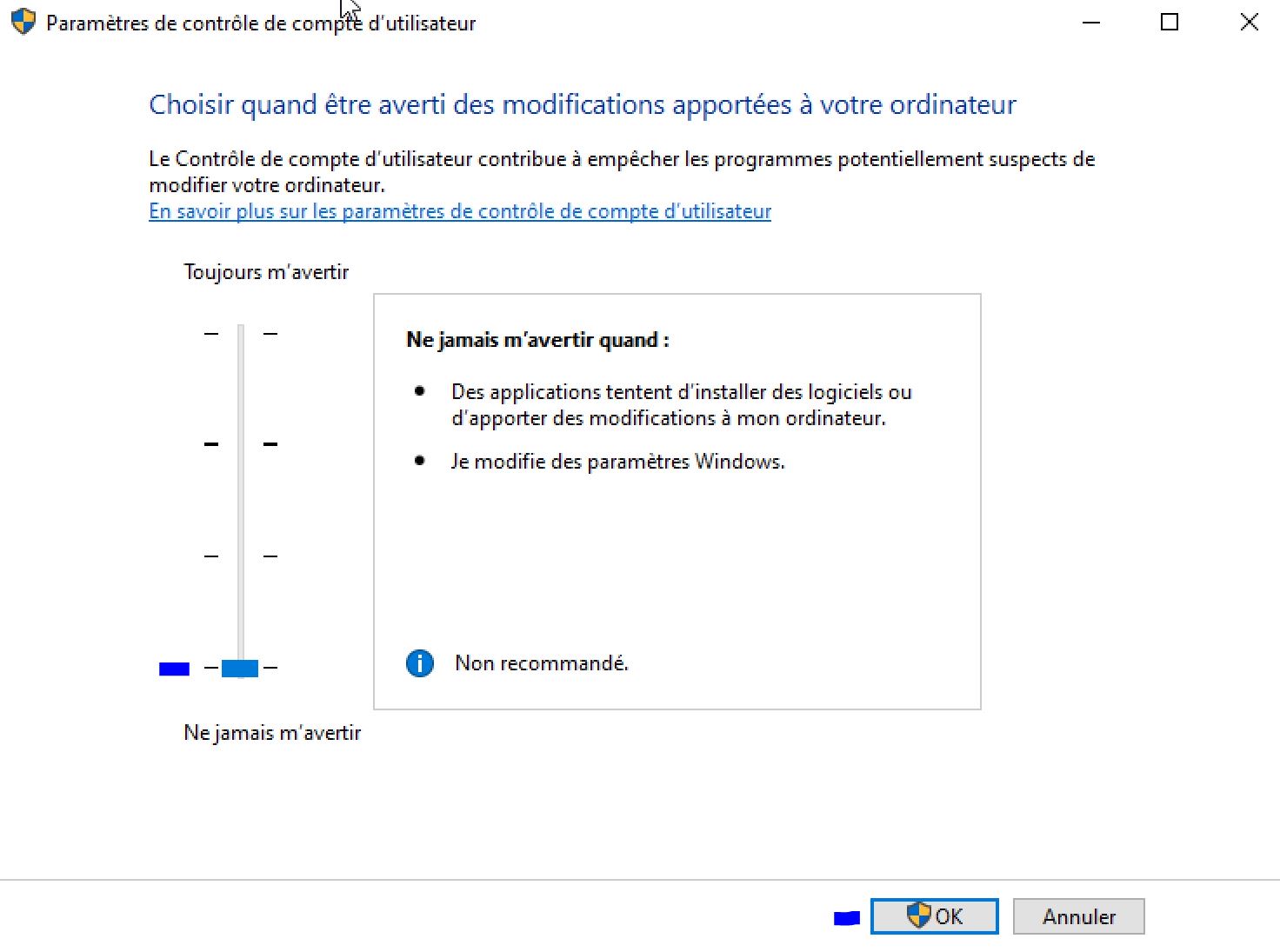
Then I diseable the notifications under the User Account Control Setting:
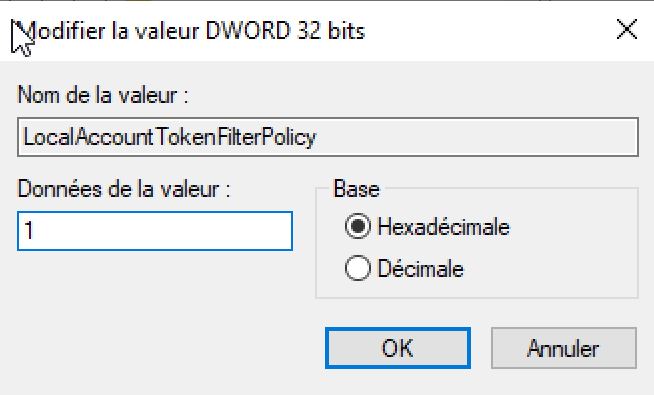
Last We'll need to add a DWORD called LocalAccountTokenFilterPolicy inside the registry editor and we have to restart the VM:
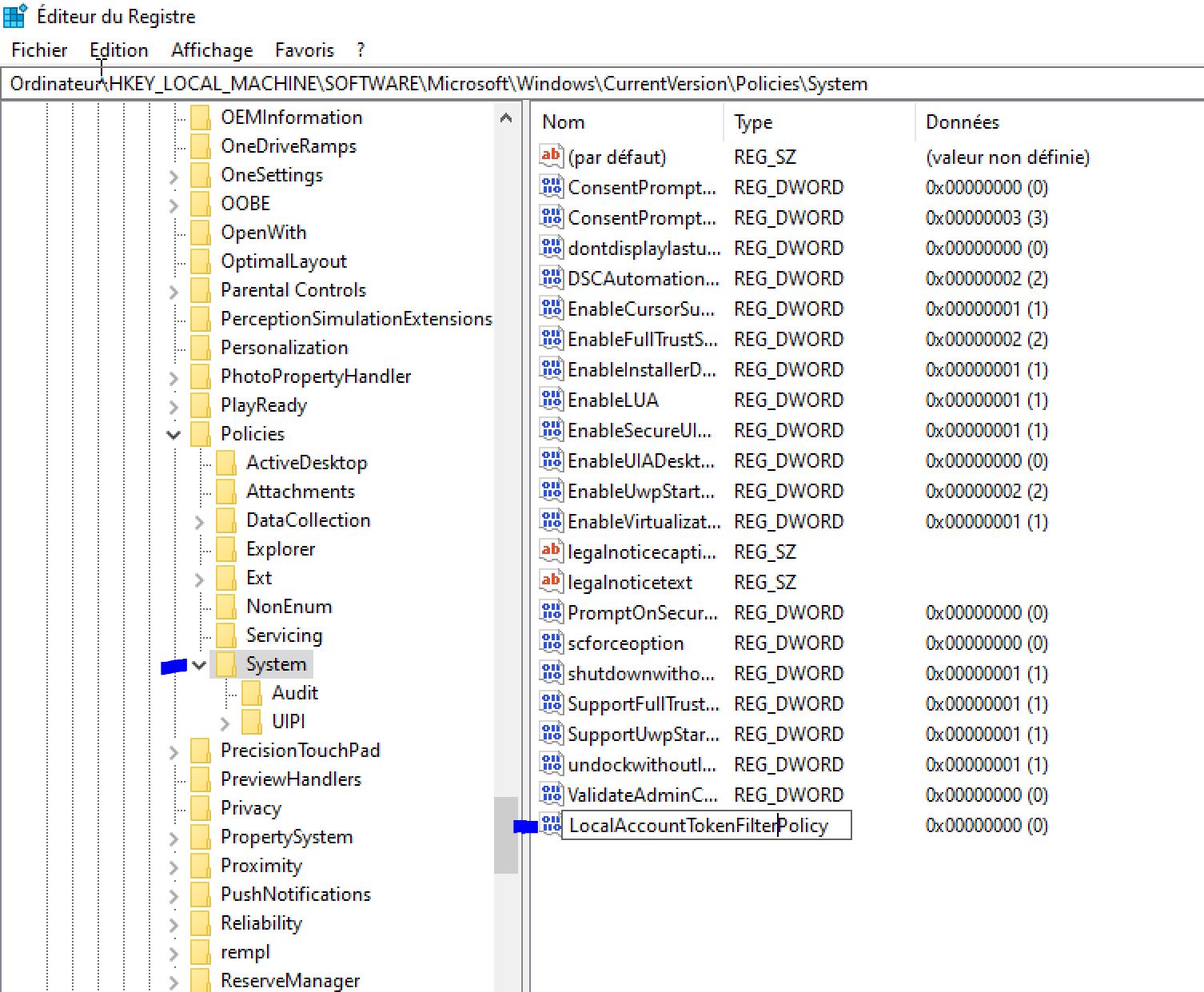
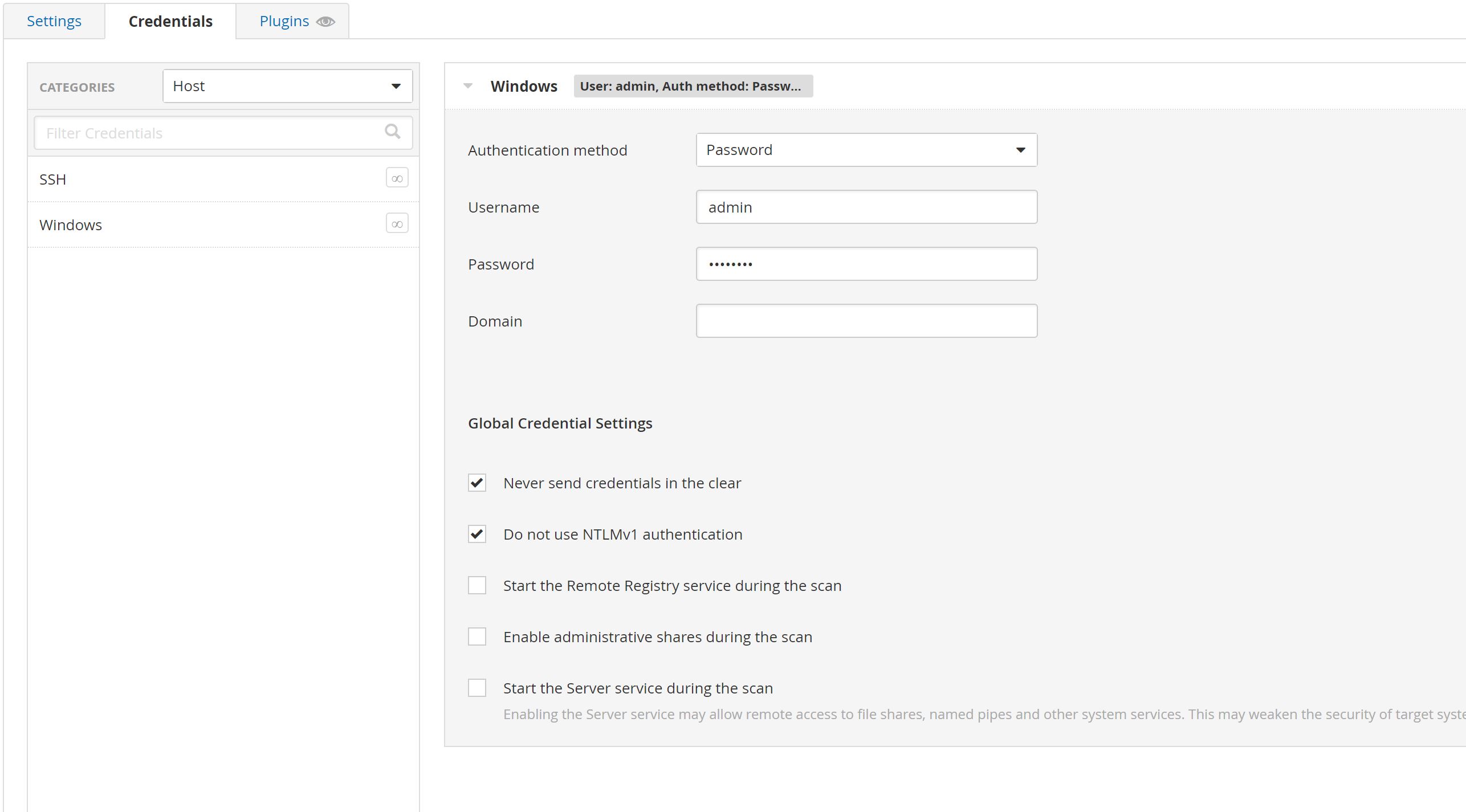
And Now we can create the Basic Network Scan with Credentials that you configured when you setup the VM:
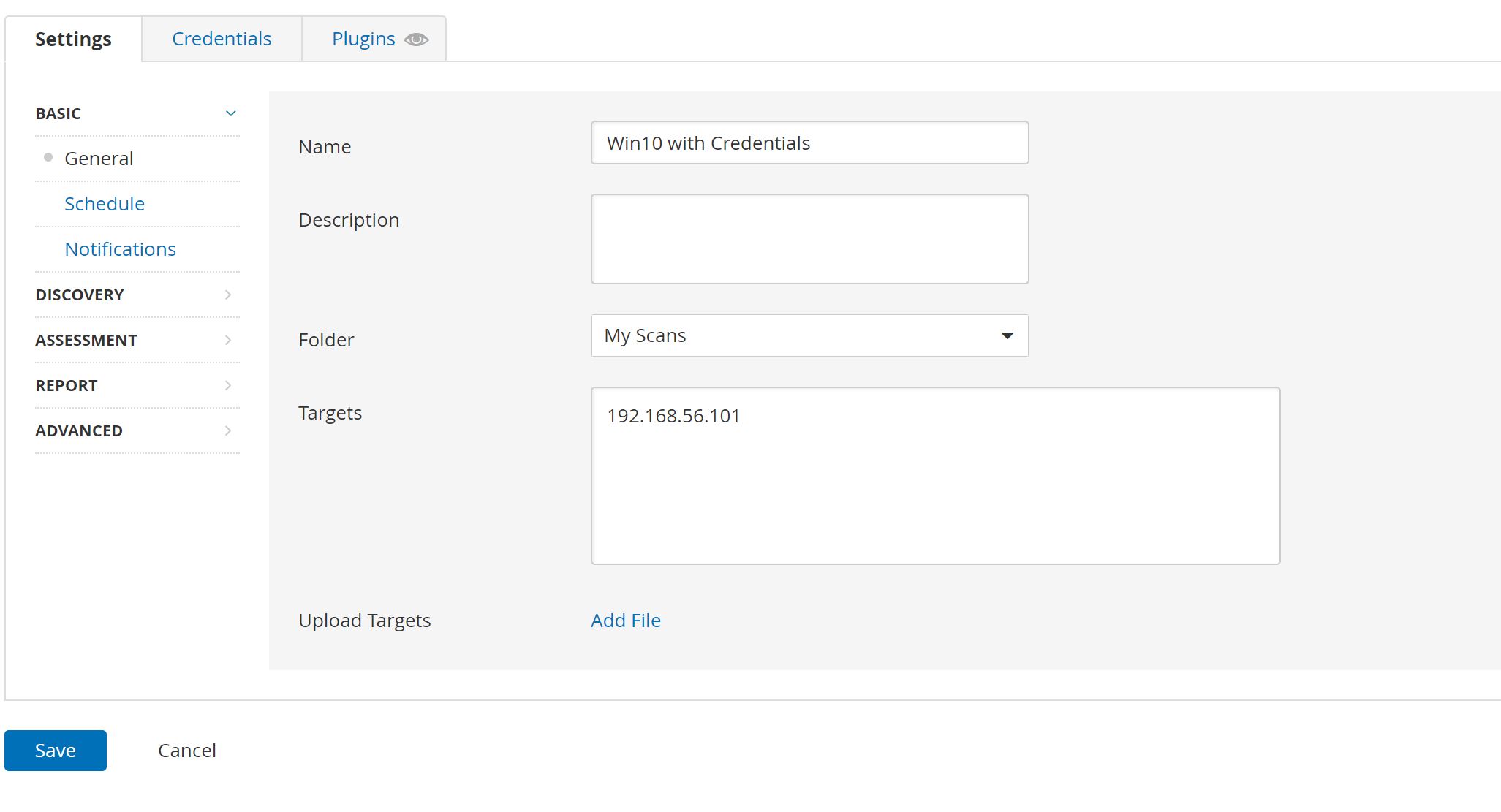
After A few minutes The scan has finished:
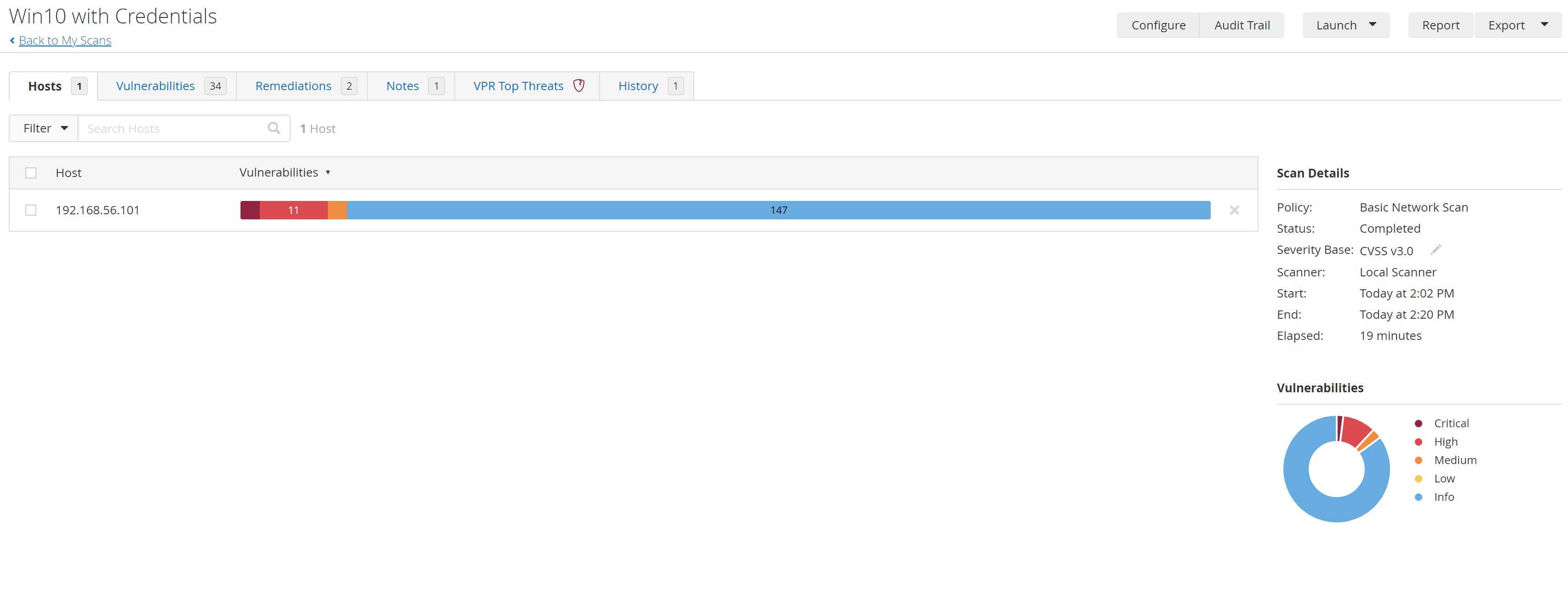
So We found 2 Critical, 11 Highs, 3 Mediums, 147 INFO vulnerabilities for example:
- CRITICAL KB5008212: that indicates that The remote Windows host is missing security update 5008212.
- HIGH Microsoft Windows VP9 Video Extensions Library RCE: The Windows 'VP9 Extensions' app installed on the remote host is affected by a remote code execution vulnerability.
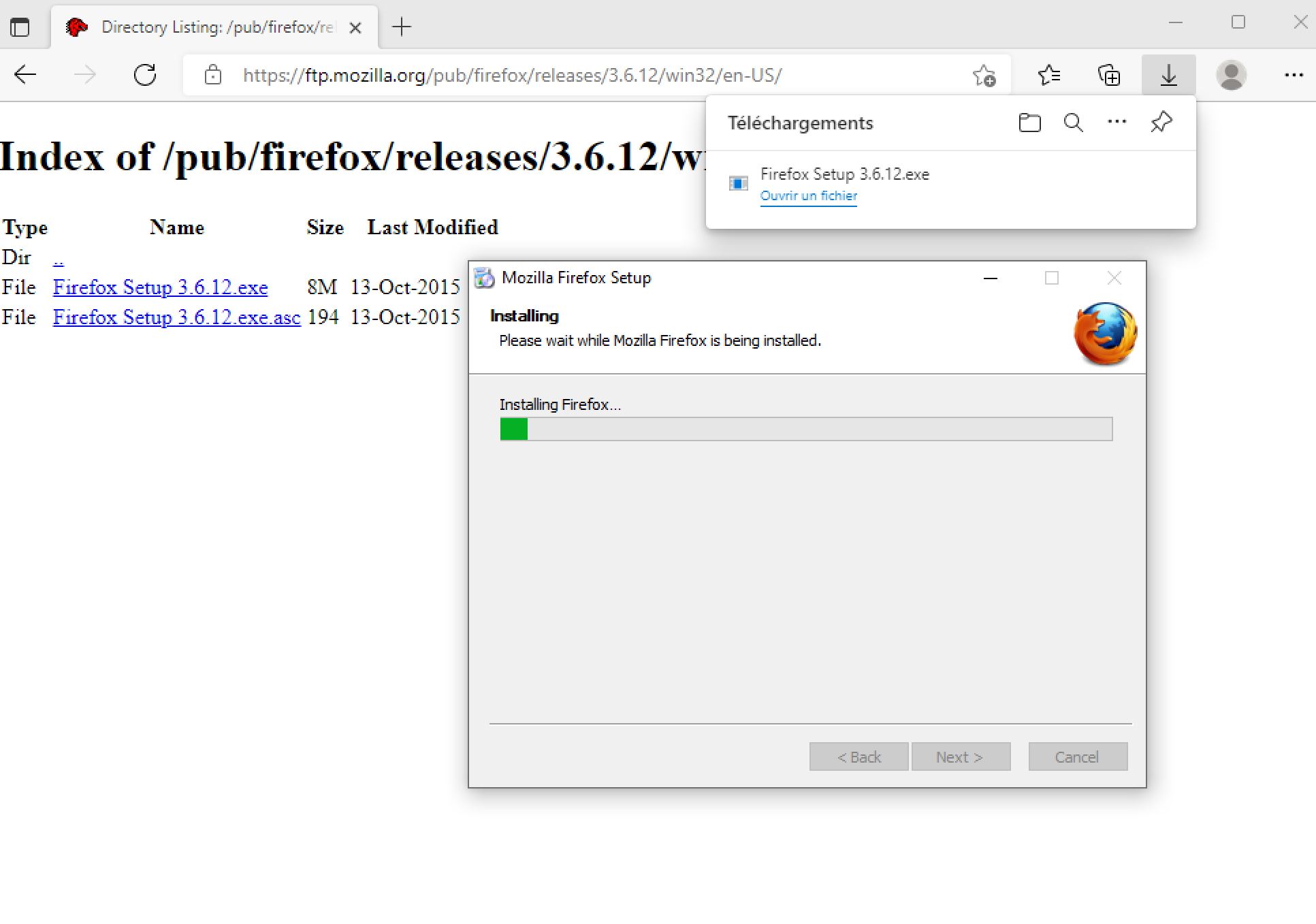
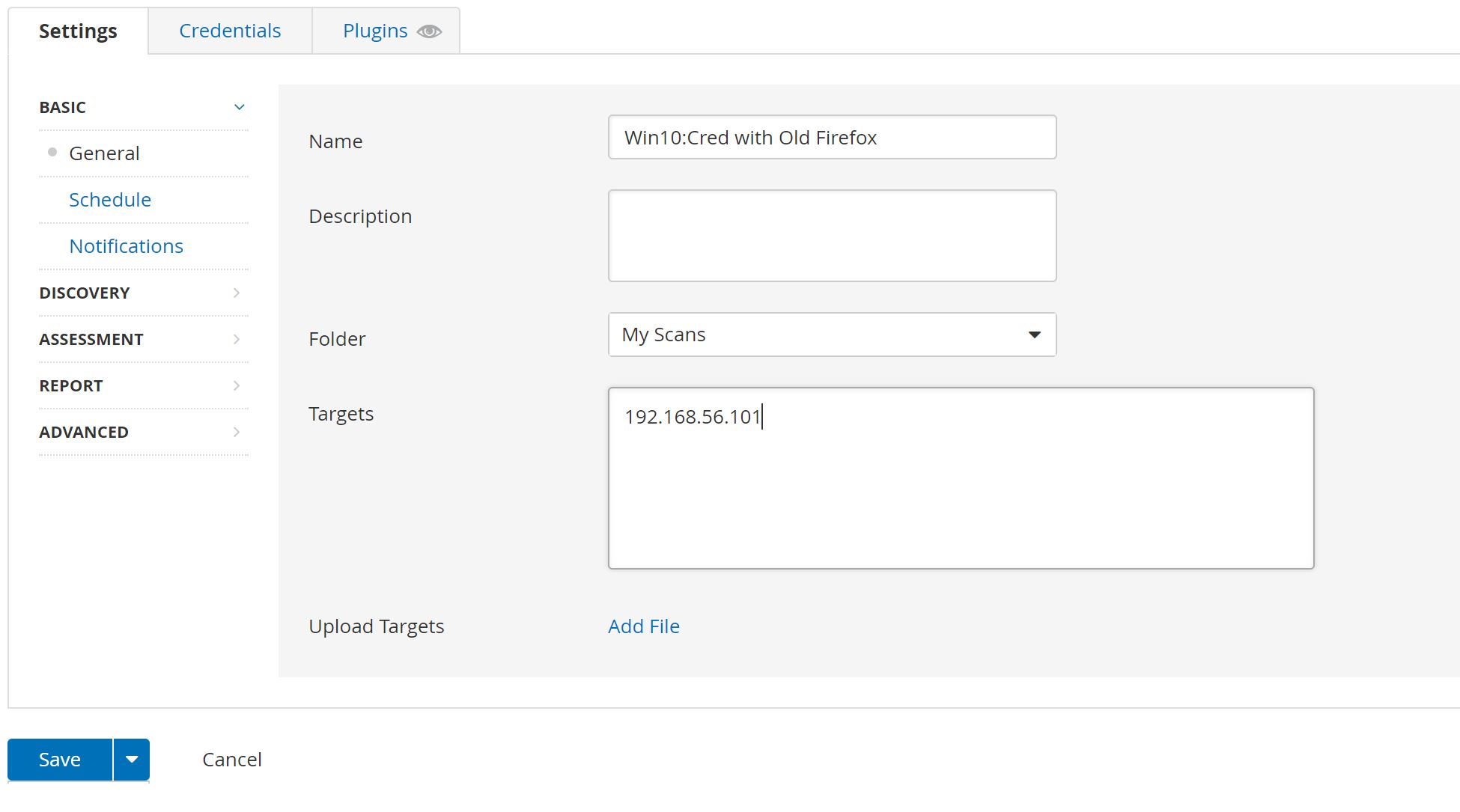
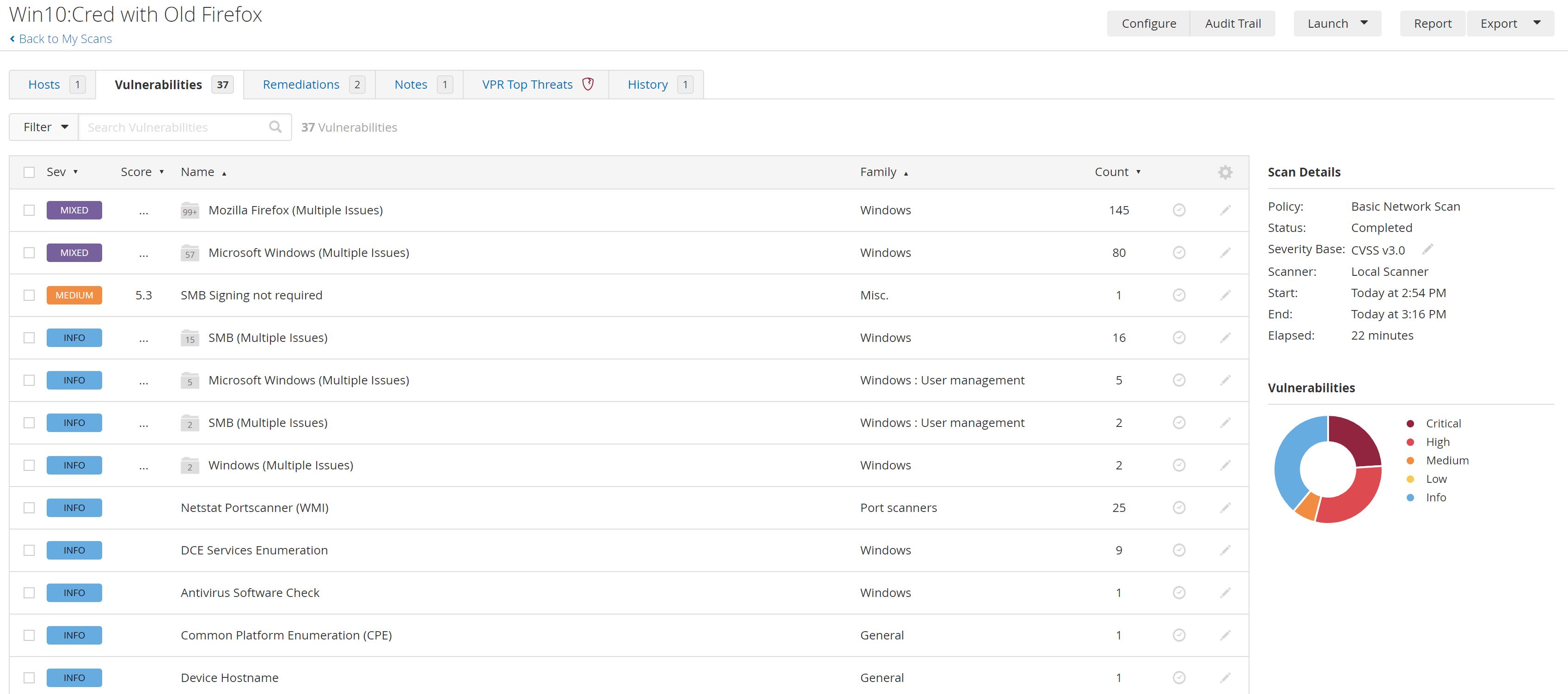
Basic Network Scan After Installing a Depricated Firefox version
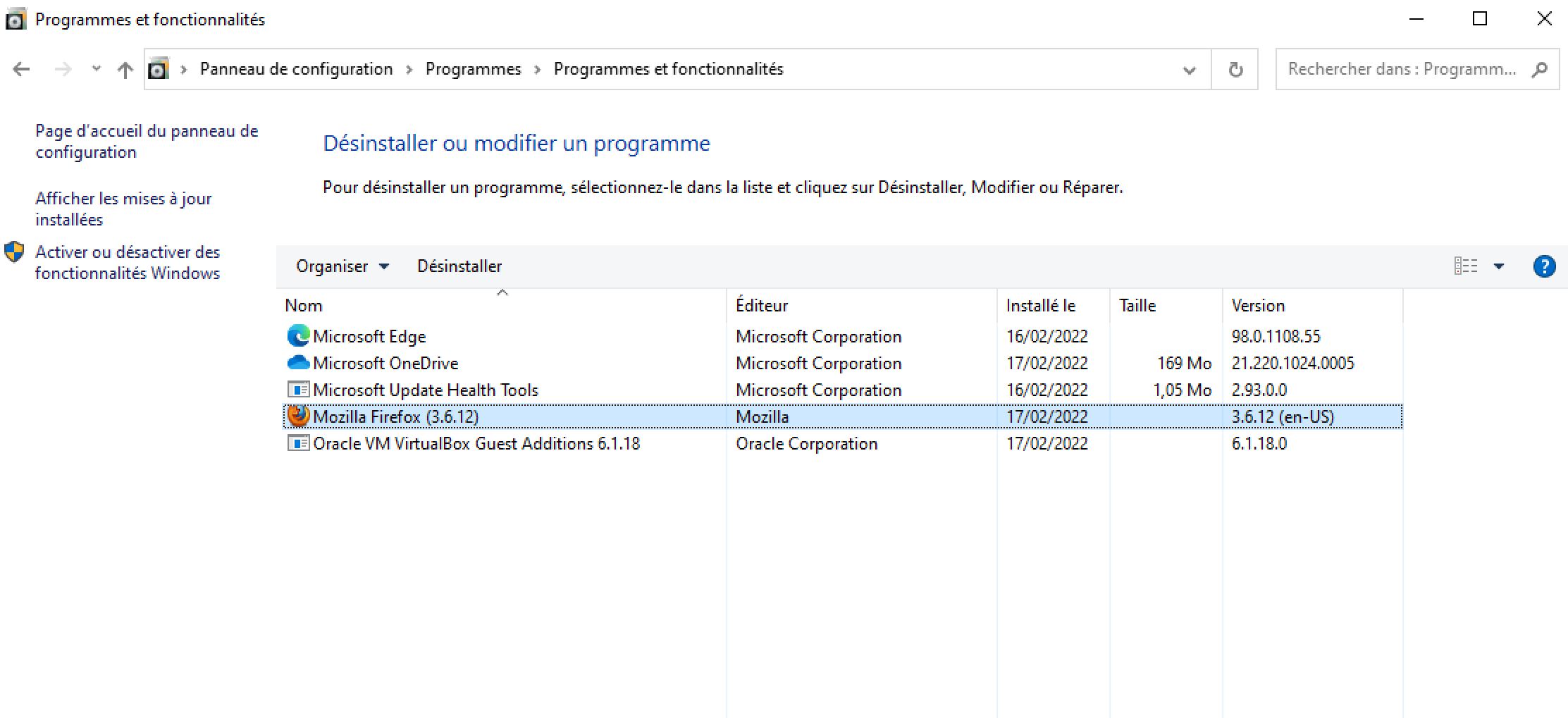
So I found this Depricated Firefox version and I've installed it in my VM.
And Now we can create the Scan
After A few minutes The scan has finished:
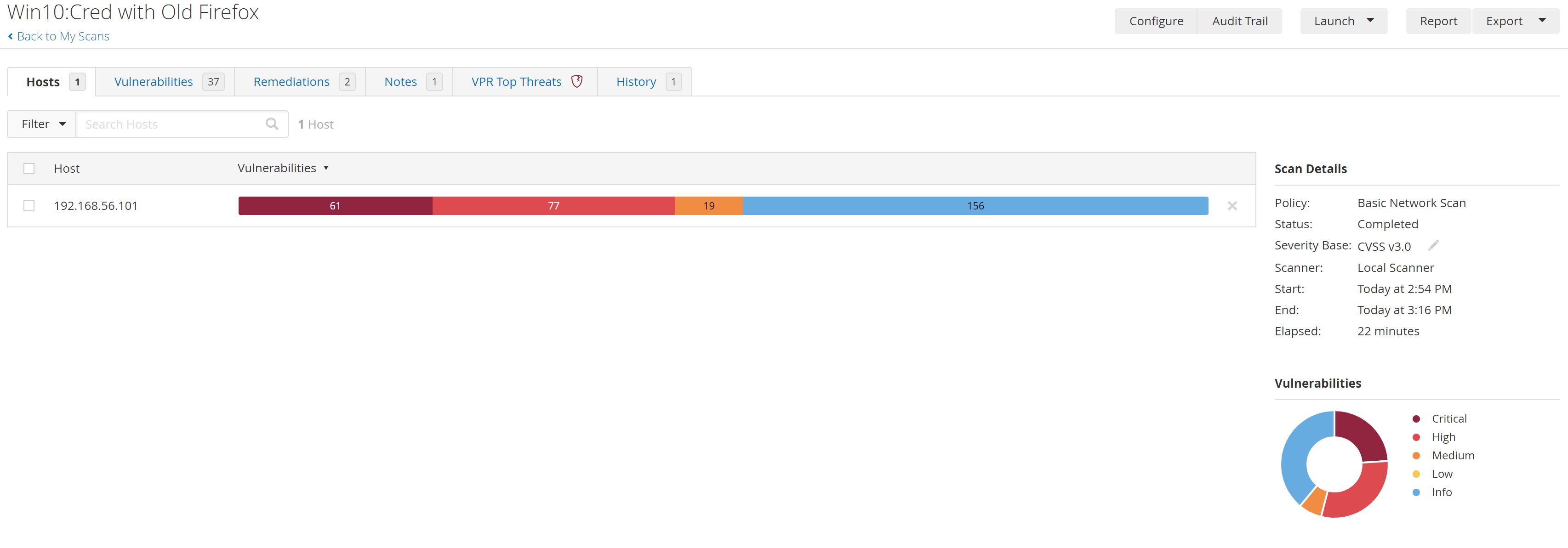
So We found 61 Critical, 77 Highs, 19 Mediums, 156 INFO vulnerabilities for example:
- CRITICAL Firefox < 14.0 Multiple Vulnerabilities: that indicates that The installed version of Firefox is earlier than 14.0 and thus.
- HIGH Microsoft Windows Defender Elevation of Privilege Vulnerability (CVE-2020-1163 & CVE-2020-1170): The version of Microsoft Windows Defender component MpCmdRun.exe installed on the remote Windows host is prior to 4.18.2005.1.
Basic Network Scan After Remediating some Vulnerabilities.
So We're gonna try to remediate some Vulnerabilities. First we Uninstall deprecated Firefox:
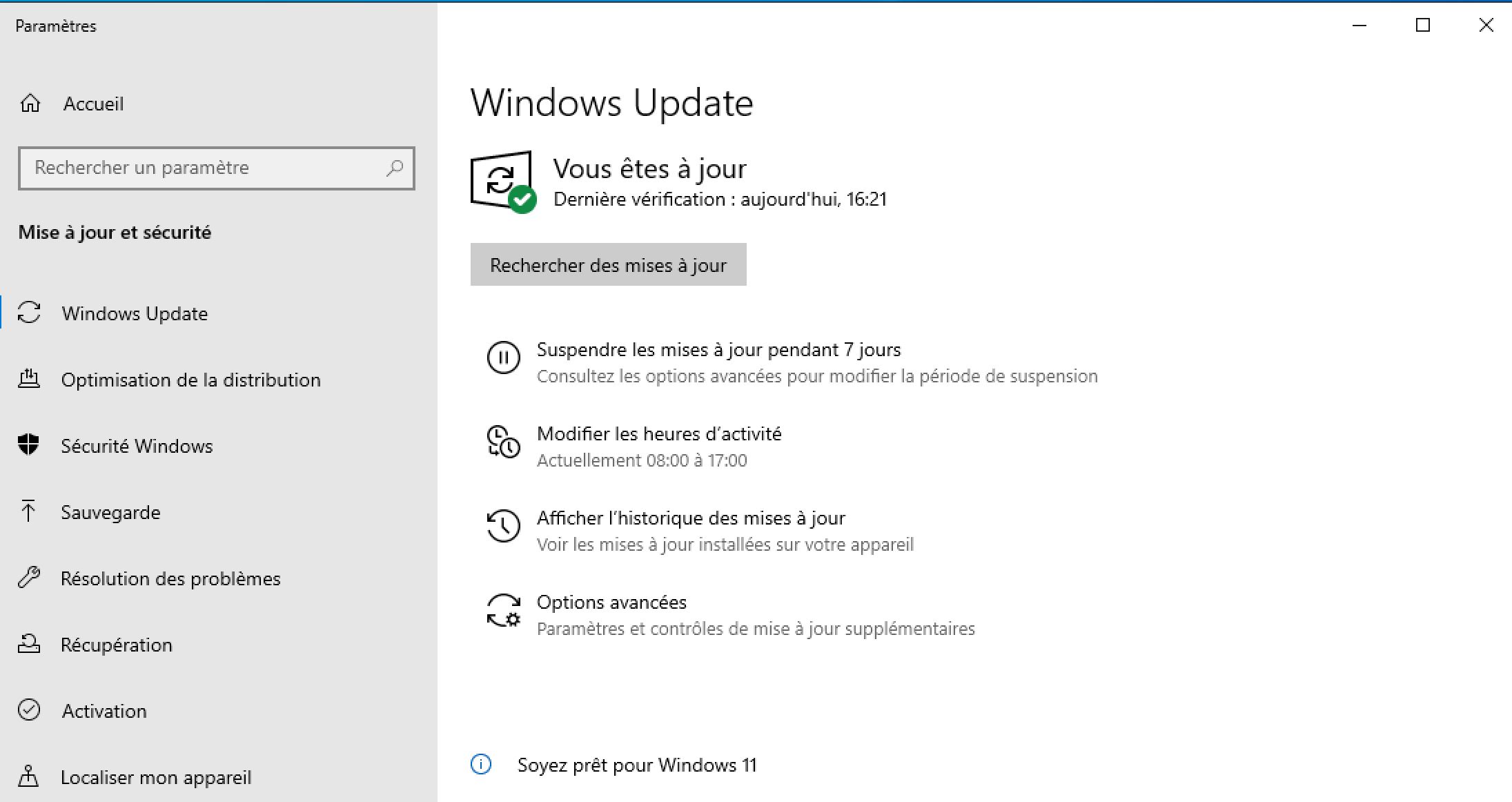
Then we update Windows:
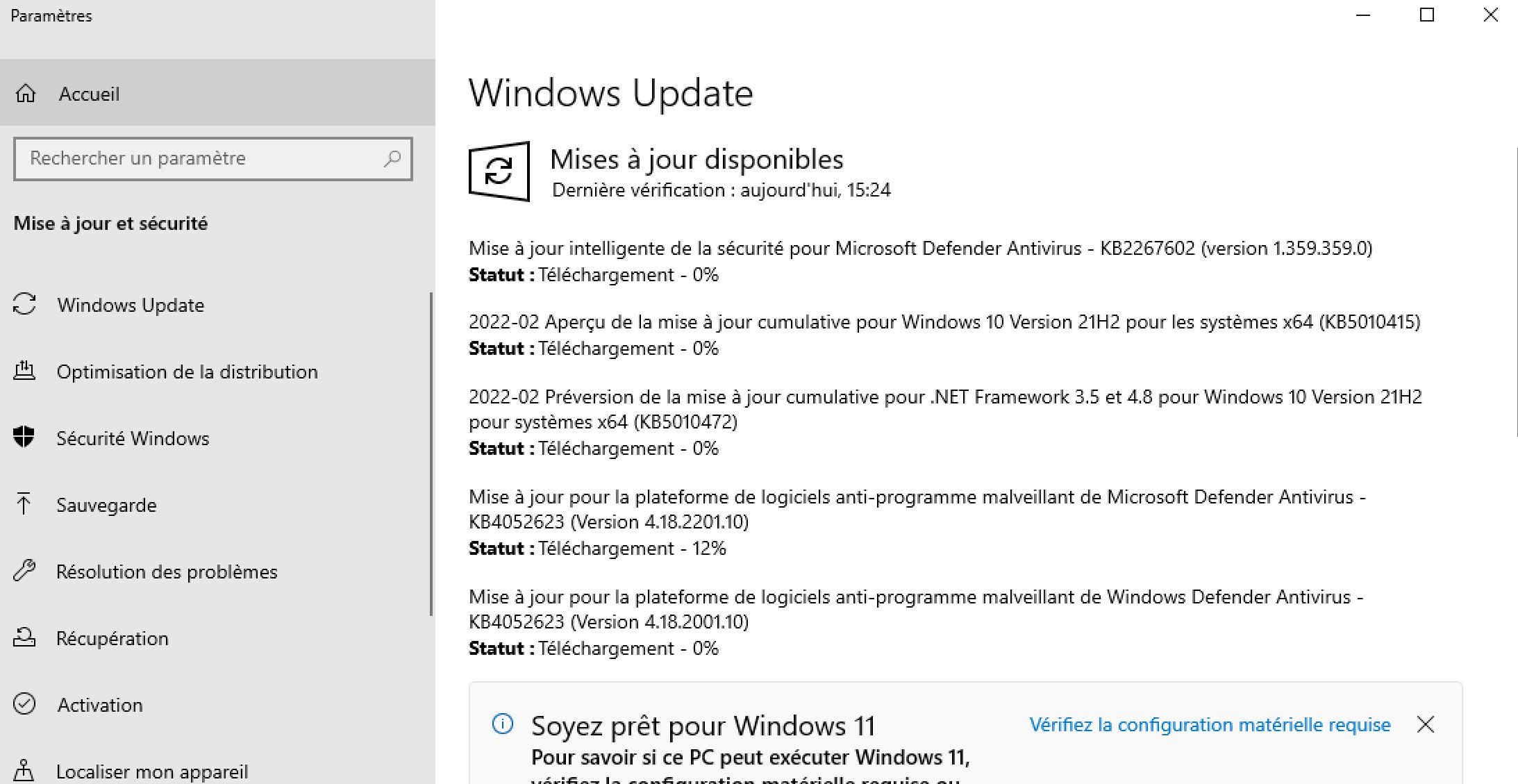
And Now we can create the Scan
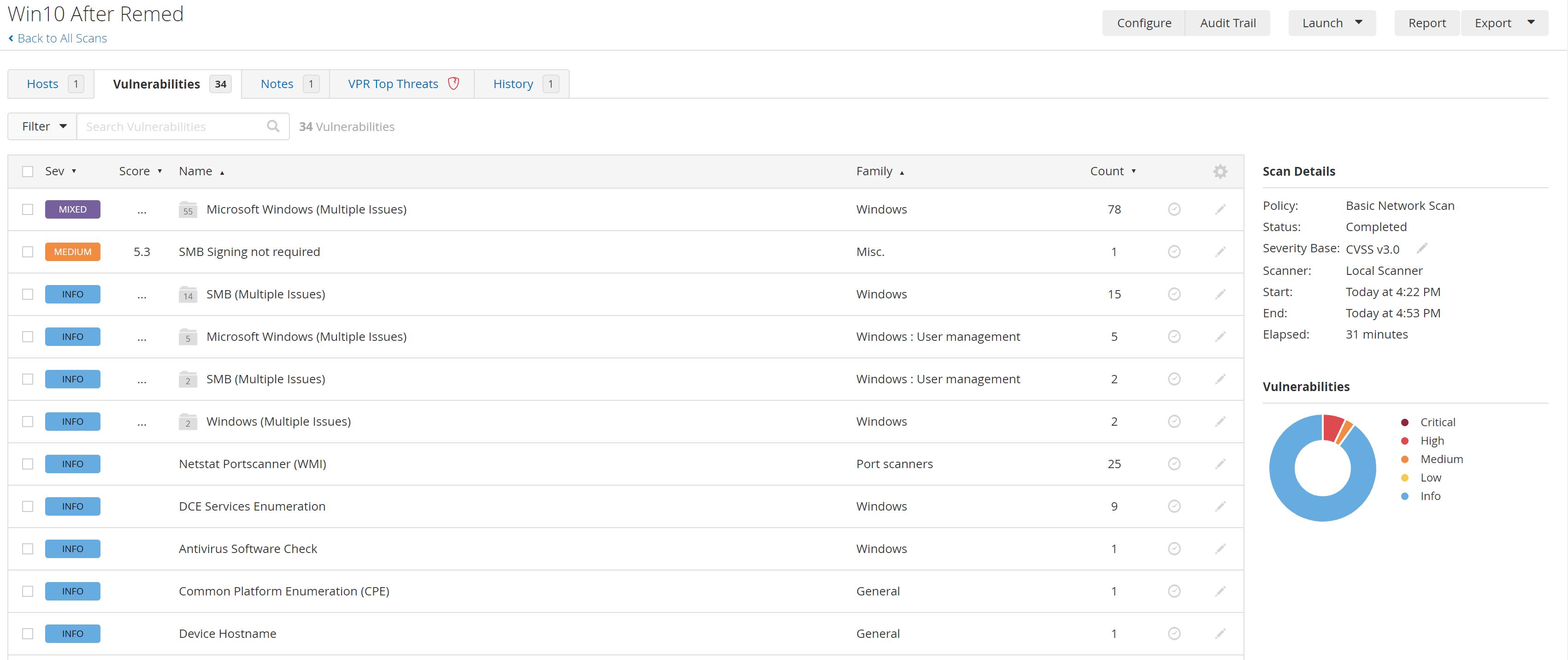
After A few minutes The scan has finished:
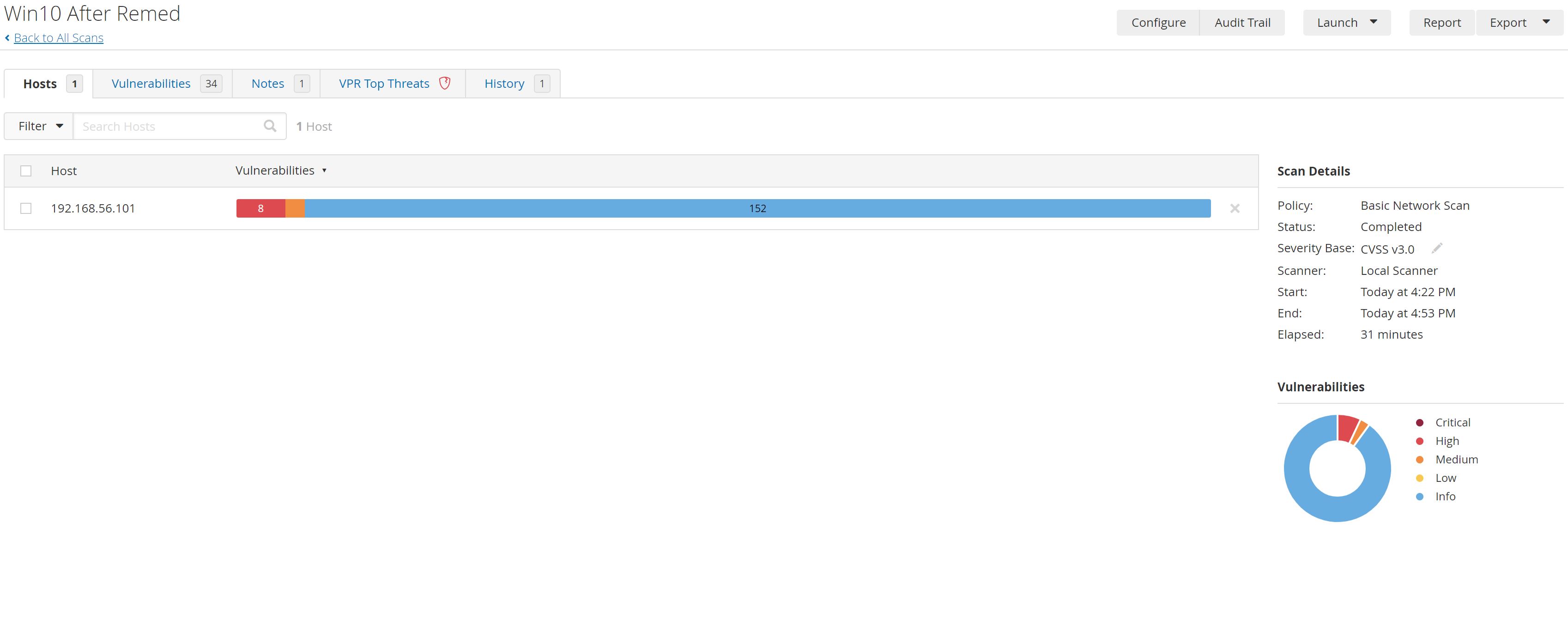
So We found 8 Highs, 3 Mediums, 152 INFO vulnerabilities for example:
- HIGH Microsoft Windows Web Media Extensions Library RCE: The Windows 'Web Media Extensions' app installed on the remote host is affected by a remote code execution vulnerability.
- MEDIUM Microsoft Paint 3D Multiple Vulnerabilities: The Windows 'Paint 3D' app installed on the remote host is affected by multiple remote code execution vulnerabilities.
Thanks for reading!!!
Reda BELHAJ
––– views